An improved version of the BlackWorm RAT has been spotted to serve the needs of the Syrian Malware Team, a group of hackers connected to the Syrian Electronic Army, possibly an offshoot of the better known collective.
The variant used by the threat actors is said to be equipped with capabilities such as bypassing the UAC (User Account Control) feature in Windows, disabling the firewall protection mechanism, as well as propagation through network shares.
Researchers at FireEye discovered that the original edition of BlackWorm has been co-authored by Naser Al Mutairi from Kuwait (njq8), a hacker Microsoft filed a lawsuit against back in June.
njq8 is also the creator of NJw0rm (also known as Jenxcus) , the malicious software that affected users from Europe and the US and led to Microsoft’s seizing of free domain names from No-IP.com.
As the BlackWorm malware was circulated on underground forums, its code received improvements from various coders, reaching the build used by the Syrian Malware Team, 2.1.
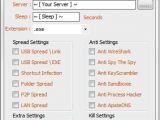
According to the researchers, this version is codenamed Dark Edition, and its builder offers better control of the built-in features, allowing operators to easily turn on or off different functions, according to their needs.
It includes options for enabling propagation through various methods (peer-to-peer, USB, shortcuts, LAN), preventing access to tools on the affected machine that could lead to disabling it, or anti-detection settings.
The choice for the binary output is also flexible, as the resulting file can be an EXE, SRC or DLL.
The Syrian Malware Team is not a new group, but they managed to fly under the radar since at least the beginning of 2011, researchers say.
It is also believed that they are involved with the Syrian government, either directly or indirectly.
FireEye analyzed samples of the BlackWorm malware and noticed references to the hacker group (“Syrian Malware” or “Syrian Malware Team”) in the communication between the binary and the command and control (C&C) server.
Their observations also determined one C&C that had been used in multiple malicious campaigns relating to Syria.
By establishing the connection between the Syrian Malware Team and the Syrian Electronic Army, security researchers painted a better picture of the entity perpetrating the attacks.
As a result, proper actions can be taken against the threat actor in order to prevent offensives against various organizations and further malware distribution.
“We connected a builder with malware samples and the actors/developers behind these attacks. This type of attribution is key to creating actionable threat intelligence to help proactively protect organizations,” says FireEye in a blog post.

 14 DAY TRIAL //
14 DAY TRIAL //