The latest Internet Explorer zero-day vulnerability (CVE-2013-3897) has been patched by Microsoft. However, experts warn that cybercriminals have used the exploit in targeted attacks since at least August 23, 2013.
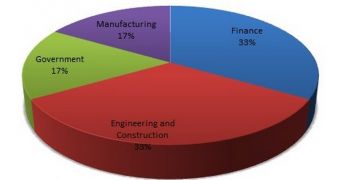
According to researchers from IT security firm Websense, the cybercriminals used the zero-day in highly targeted, low-volume attacks against organizations in the following industries: engineering and construction (33%), finance (33%), manufacturing (17%) and government (17%).
“The attacks were served by directly browsing to raw IP addresses and were spotted served by selected IP addresses in the network range of 1.234.31.x/24, which is geolocated in the Republic of Korea,” Websense’s Elad Sharf noted.
“The attack lure pages (starting point of the exploit chain) on that network range share the same URL patterns and they all consist of the URL structure /mii/guy2.html,” he added.
Interestingly, the attack pages are designed to check if the victim’s operating system language is set to Japanese or Korean before executing the exploit.
However, cybercriminals have also used an older Internet Explorer exploit (CVE-2012-4792) in their attacks. This particular exploit was triggered regardless of the victim’s operating system, browser, and language.
In fact, CVE-2012-4792 has been used to target an engineering and construction sector company and a government entity, both in the US. Expert have determined that the United States has been the most targeted geographic location (50%), followed by the Republic of Korea (33%) and Hong Kong (17%).
“It appears that the perpetrators behind this campaign target entities that belong to different industries over a selected set of geolocations, which reaffirms the notion that these kinds of campaigns operate on a global scale and focus on a variety of industries that are not necessarily related,” Sharf explained.
“The perpetrators behind these campaigns are innovative and employ zero-day exploit code, but it also appears that their work is customized for their targets since we witnessed older exploits that have already been patched being used in selected attacks.”
 14 DAY TRIAL //
14 DAY TRIAL //