Strategically important organizations, most of them from the energy sector, have been compromised in a spying campaign, giving the attackers the possibility to sabotage the affected targets.
Symantec says in a blog post that a group, which they believe to be state-sponsored judging by the resources at their disposal and their technical capabilities, has successfully infiltrated malicious programs into the systems of organizations from the energy industry.
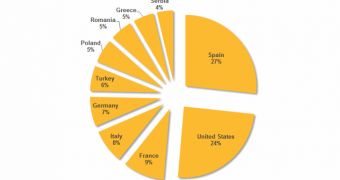
Affected by this campaign are energy grid operators, major electricity generation companies, providers of industrial equipment for the energy sector, and petroleum pipeline operators in the United States, Spain, France, Italy, Germany, Turkey, and Poland.
The attackers are known to Symantec by the name of Dragonfly and they seem to be capable of carrying out complex campaigns with the purpose of not just exfiltrating important information, but also of sabotaging the systems of the targeted companies.
The attack vector of the Dragonfly group consists in compromising the websites of the ICS (industrial control system) software providers and replacing the official file with one infected with a remote access Trojan (RAT). Victims would then download the file and infect their systems upon installing it.
This form of attack has also been reported by F-Secure at the beginning of last week. Symantec also reports that the group delivered the malware through spam campaigns and watering hole attacks. They used Backdoor.Oldrea, also known as HaveX RAT, and Trojan.Karagany.
Symantec offers some details about the modus operandi of HaveX and says that it collects information about the affected system, and “lists of files, programs installed, and root of available drives. It will also extract data from the computer’s Outlook address book and VPN configuration files. This data is then written to a temporary file in an encrypted format before being sent to a remote command-and-control (C&C) server controlled by the attackers.”
According to the researchers, the second Trojan employed by Dragonfly, Karagany, could be a modification of the original malware, whose source code was leaked in 2010. It is designed to upload information to a specific server, collect passwords, take screenshots, run executable files, as well as to catalog documents on infected computers.
Symantec's analysis comes to confirm F-Secure’s findings that the websites of three ICS software vendors were compromised and the download files were trojanized. One of the products provided VPN access to programmable logic controller (PLC) devices.
Another software package contained a driver component for a PLC type of device, while the third vendor compromised developed systems for wind turbine management.
 14 DAY TRIAL //
14 DAY TRIAL //