We’ve recently reported that Amazon has started warning its customers after they’ve identified a large number of malicious emails that relied on the company’s name and reputation. Today, GFI experts provide a sample email that’s making the rounds, attempting to lure users onto compromised websites.
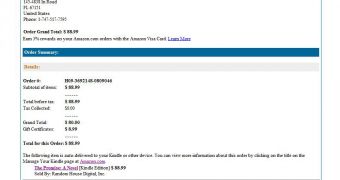
Before we get to the actual threat posed by the emails, let’s take a look at the notification to see how it can be identified as being fake.
First of all, the sender’s name (that’s right, the name, not the address) is “Amazon.com.” This makes the message somewhat legitimate-looking, but apart from this aspect, there are a lot of clues that reveal its true purpose.
For instance, even though the notification appears to be addressed to only one individual, the “To:” field shows that it has actually been sent to numerous internauts.
The fake emails contain an Amazon banner to make them appear more genuine, but as we have previously highlighted, they also contain a billing address that is most likely incorrect, or doesn’t even exist.
Finally, none of links contained in the message actually points to amazon.com, as it should. Instead, they all lead to compromised WordPress sites that host a malicious HTML file.
This file, zone.html, redirects victims to a domain that hosts the infamous Blackhole, which tries to exploit vulnerabilities in the targeted system to push malware.
While it’s clear that regular users should be wary when presented with such emails, there are some steps that should be taken by the owners of the hijacked sites in order to stop the cybercriminal operation.
Website owners, particularly the ones who manage WordPress sites, are advised to regularly update their plugins and themes. Also, they’re recommended to set strong passwords that should give a headache to hackers who rely on guesswork to compromise accounts.
Finally, webmasters should periodically check their logs for anomalies that could indicate illegal access or suspicious traffic.
 14 DAY TRIAL //
14 DAY TRIAL //