Trend Micro has published a white paper on a cybercriminal campaign called Apollo. The group that’s behind the operation uses a custom version of the ZeuS Trojan to target the remote banking systems of major Eastern European financial institutions.
One of the attacks analyzed by experts starts with a fake email purporting to come from the Ukrainian government. The notifications carry a maliciously crafted Word document that’s designed to exploit an old Microsoft Office vulnerability in order to push a .exe file onto the targeted computer.
The executable is actually a customized version of ZeuS. Once it infects a device, the malware waits for the victim to visit certain online banking websites.
When one of these sites is accessed, the threat starts logging keystrokes and capturing screenshots in an effort to harvest sensitive information which the attackers can later use to reach their goals.
Older versions of ZeuS injected fake webpages to trick potential victims into handing over their personal and financial details.
In addition to ZeuS, the cybercriminals use a variety of other tools, such as the Bleeding Life exploit pack, Pony Loader and Ann Loader.
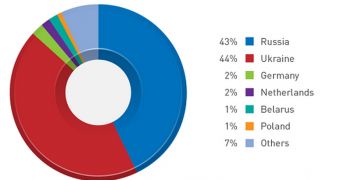
Security researchers have identified over 5,000 affected IP addresses worldwide. 43% of them are located in Russia, 44% in Ukraine, 2% in Germany, 2% in the Netherlands. Some victims are located in Belarus and Poland.
“Our research shows that while most banking Trojans target well-known banks (in the US, UK, etc), there are some that prefer a more regional and less conventional approach and by using several tools available underground, the operators were able to carry off their plans,” Trend Micro Senior Threat Researcher Jessa De La Torre noted.
“Moreover, it also demonstrates that cybercriminals are always looking for alternative ways to adapt to defenses.”
The complete whitepaper on the Apollo campaign is available on Trend Micro’s website.
 14 DAY TRIAL //
14 DAY TRIAL //