The E-Zpass toll collection system has been used as a front by cybercriminals to send out spam messages carrying URLs to malicious websites in order to increase the ASProx botnet.
Spammers are relentless in their actions and have built their “business” around a specific strategy that refreshes the lure for the victims. And since now it is the travelling season, they adapted their lure for a better rate of success.
The group behind the ASProx botnet-for-hire targeted individuals who had spent some time on the road and had to pay the toll for the road.
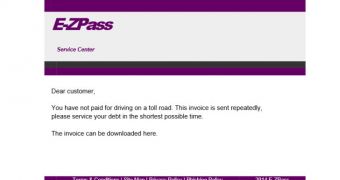
The email appears to be from E-ZPass and informs that a toll has not been paid, with a link to the invoice that needs to be paid. The URL leads to a compromised website that delivers an executable file which poses as a document, enclosed in a ZIP archive.
E-ZPass is an electronic device from the Thruway Authority that allows drivers to pre-pay their road tolls to an account, and when they move through the toll lane, the money is automatically deducted from the account after the E-ZPass is detected.
The Thruway Authority is aware of the current spam impersonating notices from them and has released a warning for drivers not to open attachments claiming to collect unpaid tolls.
Malcovery Security has identified this campaign as being initiated by the ASProx botnet operators.
They observed that the name of the malicious file sometimes contains the city and the area code the potential victim makes downloads from. This is for making the file look more legitimate.
The geo-coding system for adding the city and the ZIP code is completely automatic, and connecting to the compromised website through a VPN service automatically delivers a file with the geolocation of the VPN server in its name.
Spammers rely on a routine to deliver messages with specific content, in order to keep the lure fresh at all times.
In the case of ASProx, a botnet that is known to operate since 2008, the campaigns are very large, with as many as 10,000 messages being sent on a daily basis.
Security researchers say that this particular spam campaign was initiated on July 8 and was still active four days later. They also believe that the crooks “have a very large list of pre-compromised domains that they can use at will.”
In another campaign, the cybercriminals used the name of the Green Winick law firm to dupe users into downloading a similar type of file as in the E-ZPass campaign.
One of the purposes of the ASProx botnet is click-fraud for pay-per-click online advertising, but it can be used for other purposes as well, since the malware on the infected machine communicates with a remote server that can send it instructions.
 14 DAY TRIAL //
14 DAY TRIAL //