Cybercriminals do not care how old a vulnerability is as long as it serves their purpose, and this has been observed in recent attacks involving an Adobe Reader security flaw from May 2013 that was used to deliver the Dyre banking Trojan on insecure computers.
Dyre is also known under the name of Dyreza, and it has been seen targeting online banking customers and getting to sensitive financial information using the man-in-the-middle (MitM) technique.
Since its discovery in June this year, researchers saw it expanding the list of initial targets and being distributed mainly through malicious emails.
TrendMicro has observed roughly the same strategy recently, with the exception that the threat is delivered through an exploit for PDF files.
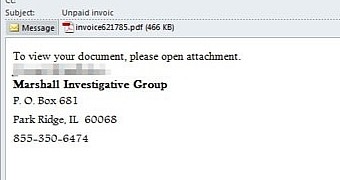
Dyre downloaded through weaponized PDF in fake invoice notification
According to the security researchers, launching the Adobe document triggers exploitation of CVE-2013-2729, which ends with downloading the Trojan.
The vulnerability affects some versions of Adobe Reader and Acrobat 9.x, 10.x and 11.x. Keeping updated software on the computer would prevent the malware from being funneled in.
From the message samples provided by TrendMicro, it appears that the email claims to deliver a notification about an unpaid invoice.
The text informs that the document has been attached and urges the user to open it and check the amount that needs to be paid and the circumstance leading to issuing it.
Bitcoin websites added to the list of targets
Dyre has been created for stealing banking information through the MitM method, which allows the attacker access to the traffic exchange between the client and the bank in an unencrypted form. In this case, this is achieved by fooling the protection mechanisms in the web browser.
However, TrendMicro observed that the new variant operated in the same way, but focused on Bitcoin websites, too.
On the list provided by the researchers, the connections to the following pages are monitored: bitbargain.co.uk, bitpay.com, localbitcoins.com, www.bitstamp.net, and the corresponding log-in pages.
The country seeing most infections, as per Trend Micro’s telemetry data, is Ireland, followed by United States, Canada, Great Britain, and Netherlands.
Researchers say that this strain of Dyre can exchange information with certain malicious websites and determine the public IP address of the compromised computer. This is useful for the attackers because this way they can pinpoint users on the map or the location of an organization.
In late September, a version of Dyre was discovered to use its own SSL certificate for communication with the command and control server, but it appears that TrendMicro caught a different sample since there is no info on this aspect.
 14 DAY TRIAL //
14 DAY TRIAL //