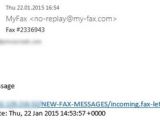
A new malicious email campaign has been observed to deliver Dyre banking Trojan to users in the US through e-fax notifications, indicating that the cybercriminals aim at infecting business computers rather than those of average users.
Despite having no technical advantage compared to email, electronic fax communication is still used in companies across the world for exchanging documents in digital format instead of paper.
Alerts for new faxes being available to the user are sent to an email inbox from the e-fax service, and a link is provided to download them.
Server-side polymorphism used to fly under the antivirus radar
In the context of the current campaign observed by security researchers at Bitdefender, the URL points to an archive that appears to contain an executable posing as a PDF file.
According to the malware analysts from the Romania-based antivirus vendor, the item is a downloader that retrieves the Dyre banking Trojan, also known under the name of Dyreza.
They observed that the operators of the campaign adopted techniques to evade antivirus detection of the downloaded malware. Cybercriminals rely on server-side polymorphism, which consists in automatically applying different obfuscation and encryption measures to the payload before it is downloaded from the malicious server, to make it appear unique.
The researchers say that in a single day, a charge of 30,000 malicious emails were delivered from spam servers in the US, Russia, Turkey, France, Canada, and the UK.
Customers of banks in different countries are targeted
During the investigation, the experts found that the campaign was named “2201us,” which could indicate the start date of the malicious operation, January 22, and the targeted country, United States.
They also discovered that the Trojan springs into action on infected computers when the victim launches websites of reputable banks in the US, UK, Ireland, Germany, Australia, Romania, and Italy.
It is common for businesses to open accounts with multiple financial institutions in order to complete money transactions more efficiently. Also, banking Trojans seek to cover as many banks as possible in order to increase their success.
Dyre relies on the man-in-the-browser technique by hooking into the web browser. It intercepts traffic between the compromised system and the targeted banks and it can manipulate the content of the website through real-time web injection.
Basically, the attackers can serve the victim fake information about the account without triggering any alarm in the web browser, since the connection appears to be a legitimate, encrypted one.
Recently, a new variant of Dyre has been spotted to include the ability to hijack Microsoft’s Outlook email client in order to spread the Upatre malware downloader, which would funnel the same Dyre Trojan on the victims' computers.
 14 DAY TRIAL //
14 DAY TRIAL //