The operators of the Cutwail spam botnet have changed their tactics and started to send the malicious emails in bursts of just a few minutes, targeting millions of users in one charge.
Security researchers have also observed that instead of malicious attachments, the emails spewed by the botnet carry links that direct to malware downloader Upatre, which funnels in the Dyre banking Trojan.
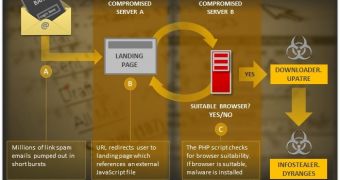
Victims either get malware or land on a phishing page
The lure follows a common pattern, where the subject line announces important communication included in the message, purporting to come from a legitimate company that may or may not be familiar to the potential victim.
Generally, emails related to some sort of financial matter (tax return, invoice, bank account statement, fines) have been seen to grab the user’s attention, making them susceptible to compromise.
Researchers from Symantec say that in some cases the links lead to phishing websites that pose as log-in pages for financial services provided by different organizations.
“The aim of the email, however, is to get the recipient to click on the included URL, which will either lead to malware or a phishing page. The attacks all use the same URL structure made up of a compromised legitimate domain,” says Nick Johnston from Symantec.
Inefficient obfuscation method used
In a blog post on Wednesday, he notes that after accessing the malicious link the user is directed to a landing page that references an external JavaScript file. The web browser of the potential victim is verified, and if it fits the profile, then the next step of the attack is initiated: getting Upatre that downloads Dyre, also known as Dyreza.
Johnston notes that the referenced URLs appear to point to legitimate JQuery files, which are common in HTML code and would not ring any alarm bells. However, they do not point to static content, as is usually the case, suggesting a dynamic web service that responds to the requests.
The researcher says that the JavaScript returned is obfuscated with JJEncode that does not work in all web browsers. The oddities do not stop here as even with this obfuscation removed, the code still includes gibberish variables and function names.
To quash suspicions of malicious activity on unsupported web browsers, the operators set up a web page filled with random words. If the browser is suitable, an archive with the malware is served.
User interaction is required to launch the threat, but since the user accessed the malicious link in the first place to get the alleged file with financial info, it is safe to assume that they would also extract the content of the archive and run it.
 14 DAY TRIAL //
14 DAY TRIAL //