Fake messages purporting to be from JPMorgan Chase banking service serves a version of Dyre banking Trojan that went undetected by any of the major antivirus engines on VirusTotal.
Dyre is a recently discovered remote access Trojan that relies on man-in-the-middle technique to route the connection between the client and the servers through cybercriminal’s infrastructure, basically controlling the communication exchange.
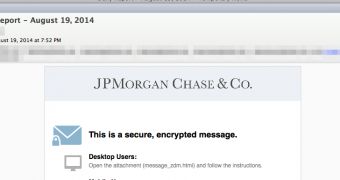
The attack vector used by the crooks is phishing, which claims to be a secure, encrypted message from JPMorgan Chase.
If the potential victims access the link provided in the email, they will be taken to a fake website of the company that asks to log into the banking account in order to view the notification; all information entered in the form is automatically sent to the crooks.
However, the danger does not stop here and an error message alerts that Java needs to be updated in order to access the account. This is just a pretext to download a fake installer that takes advantage of vulnerabilities (CVE-2012-0507 and CVE-2013-2465) in Java through RIG exploit kit.
This is possible only if an outdated version of Java is present on the system, and if this is the case, Dyre Trojan is surreptitiously added.
Researchers at Proofpoint analyzed the phishing campaign, which is deployed in multiple waves, on Friday around 150,000 malicious emails being recorded.
“What’s notable is that this is one of the first times we’ve seen an attacker include exploit code on a credential phishing page. Usually we see attackers use a Traffic Distribution System (TDS) to direct traffic to either a phishing site OR a exploit site, but not both,” says Proofpoint.
They managed to locate the server delivering the RIG exploit kit in Moscow, Russia.
It appears that the threat actors behind this campaign are actively using Dyre banking Trojan for other parallel operations, too. Other campaigns from the same attacker have been detected by Proofpoint, one of them using a PDF file weaponized with an exploit that downloads the same threat.
The operators of these campaigns are not interested in stealth, but rather in compromising as many computers as possible before laying low. Researchers say that this is the equivalent of “smash and grab” type of attack.
Using multiple forms of attack to get the banking credentials ensures a higher rate of success; even if the potential victim does not fall for the phishing trick, they are still delivered the exploit which adds the banking malware.
 14 DAY TRIAL //
14 DAY TRIAL //