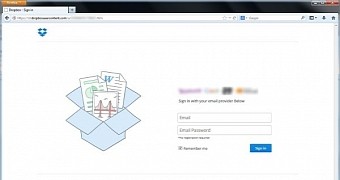
Cybercriminals trying to steal credentials for Dropbox and web-based email service have created a fake log-in page that is hosted on the file sharing website, taking advantage of its secure protocol.
The cybercriminals also included the logos of popular web-based email providers leading unsuspecting users into believing that they could also log in with the credentials for those accounts.
Credentials are sent using a secure protocol
As soon as the “sign in” button is hit, the username and password entered in the log in fields are delivered to a PHP script on a compromised server, Symantec’s Nick Johnston says in a blog post.
Sending the data to the machine accessed by the crooks is also carried out using the secure protocol, which does not raise any suspicion to the victim. Otherwise, since the fake page is accessed through an encrypted connection, the web browser would inform that an insecure communication channel is used for delivering the data, warning that it could be intercepted and read by a third-party.
Johnston says that not all the resources of the phishing page are delivered over SSL, which is marked in some web browsers by displaying a different padlock in the address bar. The change may not be observed by most users, which puts them at risk.
Method used removes suspicion of fraud attempt
According to the researcher, the email luring to the fraudulent location contains a subject suggesting that important information is enclosed.
Directing the potential victim to the malicious Dropbox location is explained in the body of the message by saying that the included document is too large to be sent over email, hence the choice for sharing it through a cloud storage service.
As soon as clicked, the share link displays the log in page, suggesting that users were signed out of the service and need to provide the account credentials to view the content.
“The fake login page is hosted on Dropbox's user content domain (like shared photos and other files are) and is served over SSL, making the attack more dangerous and convincing,” says the researcher.
This is not the first case of abusing Dropbox cloud storage service. In late August, an SMS phishing (smishing) campaign was observed relying on the same method, the difference being that the crooks delivered a fake Facebook page.
However, in the recent case, by prompting the user to log into cloud storage account through a page hosted on Dropbox, cybercriminals would be more successful because there is little to give away the scam.
Johnston informs that the service has been notified about the fraud and has taken the page down. The number of victims that have fallen for this trick is not known at the moment.
 14 DAY TRIAL //
14 DAY TRIAL //