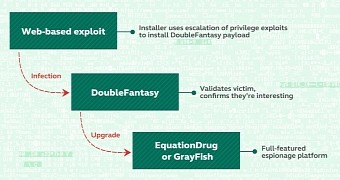
An analysis of the DoubleFantasy attack tool developed by the Equation group has been published by Kaspersky revealing that the Trojan’s purpose was to validate the victim and to allow infiltration of more complex malware.
Equation is an advanced cyber-espionage group recently discovered by Kaspersky’s Global Research and Analysis Team (GreAT), who employs sophisticated methods for gaining access to computer systems belonging to targets from sensitive activity sectors ranging from research and military to energy, telecommunication and government.
Several DoubleFantasy versions have been created
Although the malicious tool is planted on the system using advanced techniques and resources, DoubleFantasy is just the first stage of the Equation group attack, where information about the compromised system is collected to verify if it is a valid target.
If Equation finds no interest in the victim, DoubleFantasy and all its traces are removed from the system. An opposite scenario, however, would involve funneling in more sophisticated attack tools, such as GrayFish and EquationDrug.
Kaspersky found that infected computers would communicate with command and control (C&C) servers available in the configuration of the malware. They determined that one of them was located in the Czech Republic, while the other has been traced to Italy.
Multiple versions of the malicious tool have been discovered, but it appears that the most popular builds were 8 and 12.
The latter is twice the size of the former as the authors extended the functionality and added the possibility to steal usernames and passwords for Internet Explorer and Mozilla Firefox web browsers, Windows protected storage (up to XP) and the OS’s authentication subsystem on Windows Vista and above.
Scientific conference CD used to deploy attack
The security researchers found DoubleFantasy on a post-meeting CD from a scientific conference in Houston in 2009, which packed images from the gathering along with a malicious executable (autorun.exe).
In the initial stage, autorun.exe would determine the administrative rights the current user had on the machine.
If elevated privileges were needed, the malware would run three separate Windows kernel exploits in a loop; during the analysis, the researchers determined that the threat actor could add in the package up to 10 exploits and run them one after another, until the goal would be accomplished.
Kaspersky says that at the time of the incident, two of the exploits were zero-days, as the vulnerabilities leveraged were patched after the presentation CDs had been shipped.
With administrative privileges obtained, autorun.exe launches a malware dropper that installs DoubleFantasy, but not before checking for the presence of security products on the machine through registry key enumeration, a stealthier method than direct access.
“The disk used in the Houston attack represents a rare and unusual operation for the Equation Group. We presume that such attacks were crafted only for important victims who couldn't otherwise be reached, for instance, through a web-based attack vector. This is confirmed by the fact that the exploitation library had three exploits inside, two of which were zero-days at the time,” Kaspersky said on Thursday.
 14 DAY TRIAL //
14 DAY TRIAL //