System administrators and developers relying on container images shared on Docker Hub run the risk of deploying packages that contain severe vulnerabilities like Heartbleed, Poodle or the Shellshock bug for Bash command interpreter.
Docker is a lightweight container virtualization platform that allows applications written in any language to be executed in any environment, from OS X and Windows to servers in the cloud or virtual machines.
This is achieved by packaging apps in containers that include all the necessary resources for the program to run. Containers are created from a read-only image with information about its content, the processes to be executed at launch and configuration data.
A third of the analyzed images represent a high security risk
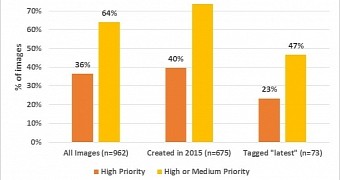
Recently launched BanyanOps, a company in the business of software container virtualization, analyzed a total of 962 images on Docker Hub and found that over 30% of those in official repositories “are highly susceptible to a variety of security attacks (e.g., Shellshock, Heartbleed, Poodle, etc.).”
Images in official repositories (about 75) are curated by a dedicated team that collaborates with upstream software maintainers and security experts. Some of them recorded hundreds of thousands of downloads.
The list of software vendors and organizations pushing official container images includes big names like Canonical, Debian and Redhat.
However, Docker users can push images themselves that are not scrutinized by any authority, and in these cases BanyanOps found that buggy packages were present in about 40% of them.
For images that are marked as being the most recent, percentage of them containing high-severity vulnerabilities is 23, while medium risk ones account for 47%.
Better vulnerability scans and management framework is needed
“Although the analysis was performed on the public Docker Hub registry, we expect that the results are very relevant to enterprises that use private registries. Enterprises typically deploy containers continuously based on golden images that are periodically updated to have the latest packages,” BanyanOps says.
The top three packages with important security risks, included in the official images, are Mercurial, the libtasn1-3 ASN library, and OpenSSL. In the case of unofficial images, the vulnerable packages are Bash, APT and OpenSSL.
While BanyanOps acknowledges the security benefits of software containers, it also highlights the need for thorough analysis of the container images for vulnerabilities (both at OS and application level) and mark for rebuild those found to be insecure. With major security flaws, a more drastic approach is proposed, that of immediate quarantine.
 14 DAY TRIAL //
14 DAY TRIAL //