Large scale virtual espionage was reveled in a recent post on the TrendLabs blog, which seems to be the true reasons for the fake certificates.
Rumors were circulating all over the web about Iranian involvement in the matter, but now, Trend Micro claims they have discovered more than 40 different ISP networks, the users of which were spied-on using the DigiNotar certificates.
The security solutions company claims they have hard evidence of the man-in-the-middle attacks which seem to have taken place mostly in Iran.
The evidence is based on the feedback data obtained through their Trend Micro Smart Protection Network, which analyzes a large number of parameters with the purpose of protecting users against future threats.
The domain called validation.diginotar.nl is the one used by internet browsers to check the validity of SSL certificates issued by the Dutch Certification Authority.
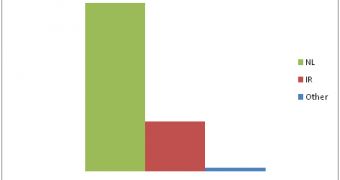
The fact which most clearly indicates that these users were targeted by these man-in-the-middle attacks is that the above mentioned domain was loaded mostly by Dutch and Iranian citizens during the chaos period at DigiNotar.
This should not have happened, as only internet users from the Netherlands and a few other countries usualy load the domain.
The chances of someone from Iran to access the web address are fairly small, the large increase of page loads proving the point.
After things calmed down, the number web rating requests made from the Asian country dropped to a normal level.
During the attacks, the information sent by the victims through services that used the rogue certificates was exposed to a third party. Some say that the Iranian government is behind this, in an attempt to spy and control their residents.
The U.S. anti-censorship software was also affected, which means that people who were making use of it may have also been victims of these attacks.
 14 DAY TRIAL //
14 DAY TRIAL //