Back in May, during the Hack in the Box 2012 security conference in Amsterdam, we had an interesting interview with Roberto Suggi Liverani about vulnerabilities in web browsers such as Maxthon and Avant.
Several months have passed and the vendors still haven’t addressed some of the vulnerabilities reported to them at the beginning of 2012. As a result, the researcher has decided to publish his findings.
The expert has published several blog posts to detail each one of the security holes he has identified.
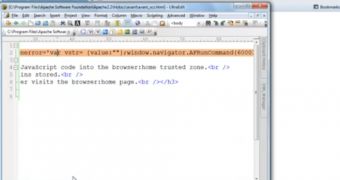
As far as Maxthon is concerned, Liverani has discovered cross-context scripting (XCS), incorrect file type handling, and same origin policy (SOP) vulnerabilities. By combining the exploitation of these flaws, arbitrary command execution is possible in four different ways.
The XCS bugs – which can be leveraged as a code injection attack vector where the injection occurs from an untrusted zone into a privileged zone of the browser – can be used against the about:history zone, the bookmark toolbar, the bookmark sidebar, the feed reader and the RSS viewer.
In Avant, the researcher has identified SOP, XCS, and stored cross-site scripting (XSS) vulnerabilities.
The bugs that plague Avant can be exploited to execute privileged commands, including for accessing the browser’s history, bookmarks and configuration.
Until these security holes are addressed by the vendors, the expert advises users to utilize other browsers.
“Since there is no patch provided by the vendor, best thing for the user is to avoid using Avant browser since it still relies on having either IE, Firefox or Chrome installed. Such browsers definitely provide a better and secure choice to the users than Avant does,” the expert told Softpedia in an email.
The technical details of these vulnerabilities, along with videos that clearly show how the flaws can be exploited, can be found on Roberto Suggi Liverani’s blog and in the advisories published on Security Assessment here (for Maxthon) and here (for Avant).
 14 DAY TRIAL //
14 DAY TRIAL //