Cybercriminals managed to compromise the popular video sharing website Dailymotion.com, by injecting malicious code designed to redirect visitors to a website that served the Sweet Orange exploit kit.
The attack was conducted by injecting an iframe into Dailymotion.com, but there is no information on how this was achieved. A common method to carry this out is to place a maliciously crafted ad from a third-party advertising network.
According to a Symantec blog post, the iframe, which became available on Dailymotion.com on June 28, would send the visitors to a different website that hosted the exploit kit.
The vulnerabilities exploited through Sweet Orange affected Java (CVE-2013-2460), Internet Explorer (CVE-2013-2551 – use-after-free remote code execution), and Flash Player (CVE-2014-0515 – buffer overflow).
If Sweet Orange found a vulnerability on the victim’s computer, it would automatically run the exploit. The user’s computer would then get infected with Trojan.Adclicker, a click fraud tool that can generate fake clicks on advertisements.
Pay-per-click (PPC) is an advertising model designed to drive traffic to the advertiser’s website. Each click on the ad earns the ad publisher some money.
In fraud cases, the publisher is actually the cybercrook, who abuses the system by generating artificial clicks for increased revenue. By targeting large communities, the cybercriminals better their chances at making more money.
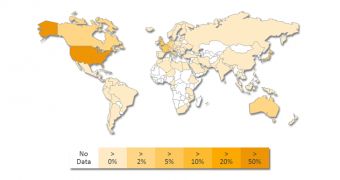
Dailymotion.com visitors from all over the world were affected by the incident, but most of them were from the U.S. and Europe, in a proportion of more than 50%. Next came visitors from Australia and Canada.
The administrators of the website have eliminated the malicious code this week and there is no risk anymore.
An antivirus solution would normally prevent the exploits delivered by Sweet Orange, but keeping software updated would also have prevented the click fraud since the exploit kit relies on older vulnerabilities that have already received a patch.
In a recent event, visitors of the Australian classified ads website Gumtree have been affected by a rogue ad. In that case, the defense mechanisms of the web browser would kick in and prevent the visitors from accessing the pages.
On June 23, Websense security researchers reported that Askmen.com had been compromised through code injection that took the visitors to landing pages for Java and Adobe Reader exploits. The kit detected at that time was Nuclear Pack.
However, after contacting Askmen.com, a spokesperson said that they did not find any malicious code on the portal. At a later time, Websense posted an update saying that they verified the website and found it to no longer serve malicious code.
 14 DAY TRIAL //
14 DAY TRIAL //