A new report on distributed denial-of-service (DDoS) attacks recorded after the first quarter of 2015 shows that some perpetrators have powerful capabilities and can carry out long-term assaults against their victims.
Data gathered by Incapsula from March 1 through May 7 (referred to by the company as Q2 2015) indicates that UDP and SYN floods continue to be the preferred method for network layer attacks and that botnet-for-hire services are responsible for shorter and less advanced incidents.
Short attacks are often used to probe defenses
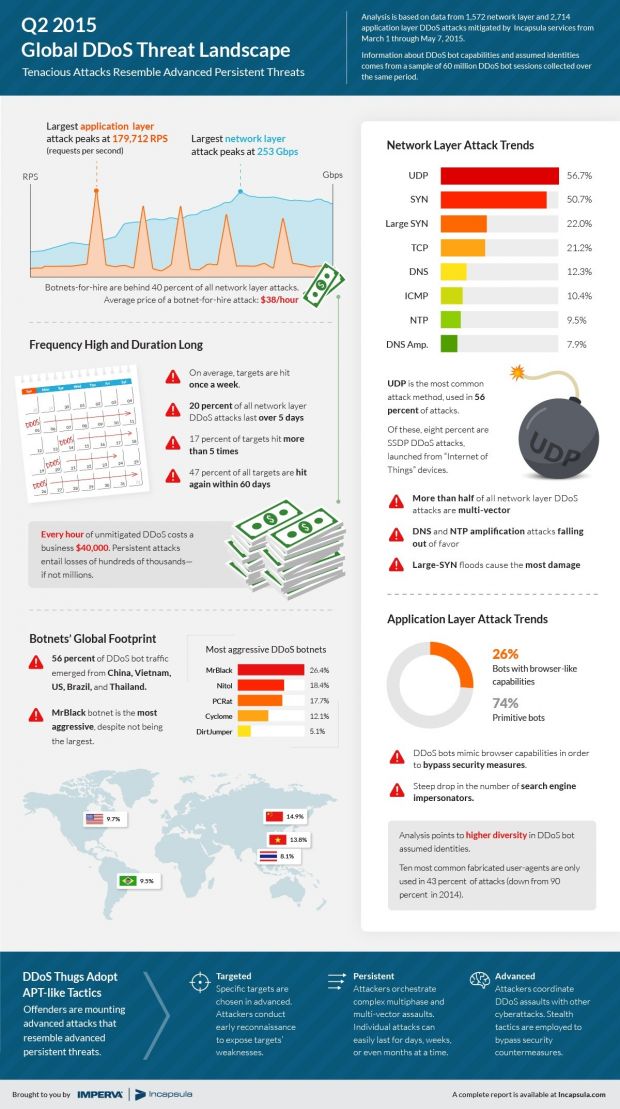
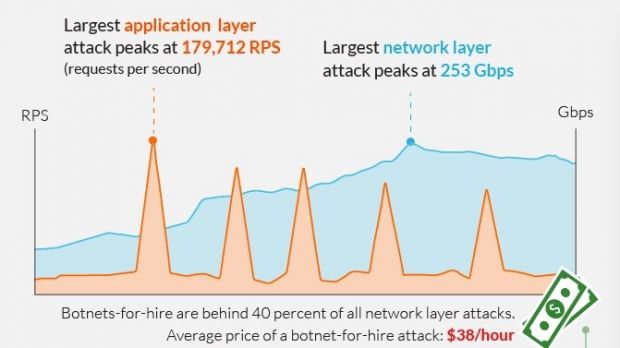
The largest DDoS event the company helped mitigate peaked at over 253Gbps, while the longest one kept pounding the victim’s infrastructure for more than 64 days.
However, such cases are not common. The high-power assault lasted for about an hour and the average was above 200Gbps.
From the 1,572 network layer attacks Incapsula pulled data from, 9.9% lasted more than 720 hours, most of them (58.1%) dying in less than 30 minutes.
The purpose of short attacks is likely to probe the target’s defenses or they are executed by inexperienced assailants via DDoS-for-hire services, the company says in a report released on Tuesday.
Extortionists may be behind large attacks
More extended events that last at least one day suggest that the perpetrators are skilled cybercriminals who control their own botnets. Such groups may engage in blackmail operations, threatening victims with congesting their resources unless they pay a fee.
Recently, governments and CERT (Computer Emergency Response Teams) divisions in multiple countries issued alerts about a group called DD4BC, who boasts capabilities for UDP flood attacks of at least 400Gbps against selected targets unless 40 bitcoins (currently approximately $9,100 / €8,100) are paid.
Incapsula says that out of more than 56% of the UDP and SYN floods seen in the studied time interval, 8% are launched from “Internet of Things” devices, indicating that the cybercriminal effort to expand their resources covers any gadget capable to connect to the web.
As far as application layer attacks are concerned, perpetrators’ tools of choice are MrBlack, Nitol, PCRat, and Cyclone malware.
In the largest incident of this sort recorded by Incapsula, almost 180,000 requests were sent every second, while the longest extended for a period of eight days.
 14 DAY TRIAL //
14 DAY TRIAL //