After members of the Tor Project revealed that they found a vulnerability in Cyberoam’s deep packet inspection (DPI) devices, which could allow for traffic to be intercepted, the company responded to the allegations to reassure customers that it was unlikely for this to happen.
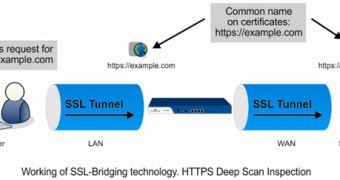
“HTTPS Deep Scan Inspection is driven by SSL Bridging Technology. In SSL Bridging, Cyberoam appliance provides self-signed certificate to the client whilst establishing a secure connection with the client and server. Hence, Cyberoam can now scan the SSL traffic for malwares,” the firm said regarding the technology it uses.
“This is the only legitimately acceptable approach being followed by the network security vendors. TOR also acknowledges the same. A default certificate is shipped which remains the same across all the appliances.”
However, they claim that the private keys utilized in SSL Bridging are variable, only the public keys being the same.
Since the importation or exportation of private keys is not allowed by the vendor, the decryption of SSL data is impossible.
“Cyberoam UTM either accepts or rejects, but does not store HTTPS Deep Scan Inspection data, as processing is done in real-time. The possibility of data interception between any two Cyberoam appliances is hence nullified,” company representatives added.
Fortinet and SonicWALL may be using the same approach, but many believe that this isn’t actually a vulnerability.
“Yes Cyberoam is using a man-in-the-middle approach to scan HTTPS traffic, but it is not hidden to his customers. Customers have the choice to activate or not this feature. If they don't trust in Cyberoam, they just don't activate the feature. This feature is not activated by default,” an Anonymous user explained in the comment section of Tor’s post.
Tor Representatives have yet to respond to Cyberoam’s statement.
 14 DAY TRIAL //
14 DAY TRIAL //