One of the update mechanisms of the infamous Conficker worm is set to come into action on April 1st, resulting in a real media hype. As misinformed users are frenetically searching for information about the alleged threat, various online criminals are leveraging on this interest to promote pages leading to malware.
Conficker, also known as Downadup or Kido, is currently the most intriguing worm out on the Internet for a variety of reasons, one of them being, ironically, that it doesn't do anything. Up until now, its creators have been more preoccupied with maintaining the worm, instead of giving it a real purpose, leading to a lot of speculation.
Clearly, the massive botnet counting millions of infected computers can be used for a variety of malicious things, like sending spam and phishing e-mails or launching denial of service attacks. Its creators might use it themselves or rent portions of it to other cyber-criminal groups as part of a malware-as-a-service type of operation, but this uncertainty has put professionals on constant alert.
The worm has several update mechanisms, one of which involves generating random domain names, which it then queries on a daily basis in order to receive instructions. Each daily generated list consists of 50,000 domain names, but the worm has not started connecting to them in search of a command and control server. This is set to start happening beginning with April 1st.
The truth is that no one knows what will happen on that day, but many security researchers claim that chances of something major occurring are slim to none. There are several arguments that support this theory. For one, the worm has other update mechanisms in place, which its authors have already used to update it to variant C on a number of systems.
Additionally, the latest version of the worm introduces peer-to-peer capabilities, which means that each infected computer can act as a relay for instructions, making the need of a central command and control server obsolete. Furthermore, it would make no sense for the Conficker authors to command the botnet to do something drastic and really damaging like deleting everything on the infected computers or even messing with their operation. Their actions until this point have reflected a strong desire to keep it running.
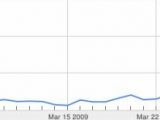
Graham Cluley, senior technology consultant at Sophos, has posted a Google Trends graph showing a drastic increase in searches for "Conficker," starting with March 22. "Clearly, as the media has published (sometimes hysterical) stories about Conficker and April 1st, more and more people have turned to Internet search engines to find out more information," he explains.
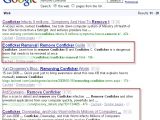
Unfortunately, security researchers such as Mr. Cluley are not the only ones checking Google Trends, malware distributors making heavy use of it too. Basically, they are constantly checking the most popular search keywords and are populating their malicious pages with them in order for them to appear higher in search results, thus increasing the pool of potential victims. Such practices are known as black-hat search engine optimization (SEO) techniques.
Rik Ferguson, solutions architect at Trend Micro, warns that many of the top Google search results for Conficker removal tools and instructions have been compromised in this way. "If you need malware removal tools, type the URL of your vendor of choice directly into the browser bar and use links on their website. Do not rely on Google search results at this time, as they may have been 'optimised,'" the security expert advises.
Meanwhile, Patrik Runald, senior security specialist at F-Secure, issues a similar warning pointing out that scareware advertisers are using the whole Conficker hype to promote rogue security applications. "Get your facts from known sites and download your removal tools from respected companies," he writes.
Mr. Runald is backed up Georg Wicherski, virus analyst at Kaspersky Lab, who has noticed the same problem, but he also adds that, "These are not the only people trying to make money from public fear of this supposed new mega-worm." He advises that, "Other people for example are trying to sell their assistance in removing Kido from computers on a certain website. Do not provide them with your real data, there are utilities to help you available for free."
Here are the links for some legit Conficker removal tools (pick your favourite vendor):
Kaspersky: Net-Worm.Win32.Kido Remover BitDefender: Win32.Worm.Downadup Removal Tool Symantec: W32.Downadup Removal Tool F-Secure: F-Secure Easy Clean McAfee: McAfee AVERT Stinger Conficker Sophos: Sophos Conficker Clean-up Tool Trend Micro: Trend Micro System Cleaner

 14 DAY TRIAL //
14 DAY TRIAL //