Ramsomware has become one of the biggest threats to Internet users and, considering that cybercriminals can make millions of dollars each year by relying on such pieces of malware, it’s clear that they’ll invest some time and resources into making them better.
At first, they incorporated audio files which played the threat message. Now, to ensure that their creations have a better chance of evading digital signature checks, they’ve signed them with fake certificates.
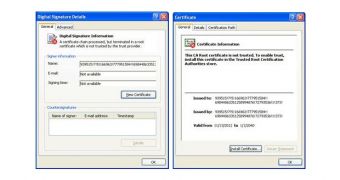
Trend Micro experts have come across a couple of samples, identified as TROJ_RANSOM.DDR, both signed with a suspicious name and issued by a suspicious provider.
One of the samples relies on the FBI to scare internauts into paying a fine if they want to see their computers unlocked, while the other one uses the reputation of the UK’s Police Central e-Crime Unit.
The newer variants lock up computers and threaten victims with messages based on their geographic location. The language used to demand the payment of fines is adapted and so is the name of the law enforcement agency.
Over the past years, cybercriminals have started relying more and more on expired or fake digital certificates. Unfortunately, this doesn’t apply only to ransomware, but to all sorts of malware.
Flame utilized certificates to sign some of its components and, more recently, even Adobe-issued certificates were used to sign malicious utilities.
 14 DAY TRIAL //
14 DAY TRIAL //