Everyone’s talking these days about the “APT1: Exposing One of China's Cyber Espionage Units” report released by Mandiant. Cybercriminals are also leveraging the story in an attempt to spread a piece of malware.
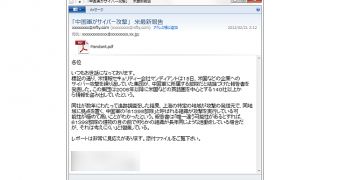
According to Symantec, it all starts with an apparently innocent email that contains an attachment called “Mandiant.pdf.” When opened, a blank PDF is shown, while an Adobe Reader exploit is triggered in the background.
Interestingly, the exploit analyzed by Symantec failed to drop any malware onto the computer. However, Brandon Dixon, a security intelligence engineer at VERISIGN, has identified a different variant.
In his case, the attachment, a file called “Mandiant_APT2_Report.pdf,” was password-protected. When executed, the genuine Mandiant report is opened, while a new process is executed.
The payload connects to a domain that’s been previously seen in attacks against human rights activists. The domain in question was flagged as hosting malware on both Mac and Windows systems.
 14 DAY TRIAL //
14 DAY TRIAL //