Cybercriminals are coming up with new ways to ensure that the malware they create can communicate with command and control (C&C) servers. Symantec experts found that they’ve started using the Sender Policy Framework (SPF) to maintain a solid connection between the malicious element and the C&Cs.
SPF, an email validation system which allows administrators to block spam emails, relies on DNS requests and responses. If the DNS server used to send the email is configured to use SPF, the DNS response contains a SPF record that’s specific to each legitimate website.
“The point for the malware author is that domains or IP addresses in SPF can be obtained from a DNS request and this DNS request doesn’t need to be requested from a computer directly. Usually the local DNS server is used as a DNS cache server. The DNS cache server can send a request instead of the computer,” Symantec’s Takashi Katsuki explained.
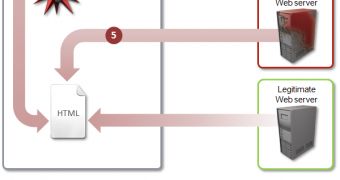
So, when this malware – identified as Trojan.Spachanel – infects a computer, it makes a DNS request with a generated .com or .net domain. This request is sent to the local DNS server, which forwards it to the attacker’s DNS server.
This server returns a response containing a SPF record. This record holds the malicious domains and IP addresses needed by the malware to operate.
Once this is accomplished, the Trojan injects itself into the web browser process and monitors Internet traffic, and injects malicious code into the websites loaded by the victim.
This code generates advertisements which help the cybercriminals make a profit.
This is not the first time we learn of pieces of malware that use legitimate services for communications. Back in November 2012, Symantec experts detailed a piece of malware which used the viewer function in Google Docs as a proxy.
 14 DAY TRIAL //
14 DAY TRIAL //