The developers of the Android Trojan dubbed Svpeng (Trojan-SMS.AndroidOS.Svpeng) have enhanced their creation. The malware can now be used for mobile phishing attacks.
According to researchers from Kaspersky, once it infects a mobile device, the threat waits for its owner to launch the banking application of a major Russian financial institution. When the app is opened, the Trojan injects a phishing page where users have to enter their login ID and password.
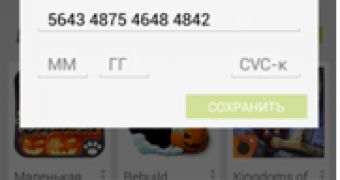
In addition to stealing banking details, the malware also targets Google Play. When the Android market app is launched by the victim, another phishing page is injected. This time, the phishing window asks for payment card details such as card number, expiration date and CVV.
In both cases, the information entered by the user is sent back to a server controlled by the cybercriminals.
However, that’s not all this Trojan can do. It sends SMS messages to two major Russian banks to see if there are payment cards attached to the infected phone’s number. If a card is attached to the compromised phone, the cybercooks can send commands to transfer money from the victim’s account to their own.
Currently, the malware is designed to target only Russian users. However, experts warn that it might be rolled out in other countries as well, especially since Svpeng is already designed to check the operating system's language versions.
So far, Kaspersky has spotted 50 variations of the threat that's distributed via SMS spam.
Another noteworthy thing about Svpeng is that it uses the DeviceAdmin Android tool to protect itself against antivirus solutions. Victims are prevented from disabling DeviceAdmin or resetting the smartphone to factory settings. For this, the threat exploits an Android zero-day.
Additional technical details on Svpeng are available on Kaspersky's blog.
 14 DAY TRIAL //
14 DAY TRIAL //