Cybercriminals have come up with an interesting way of getting Brazilian users to install a banking Trojan on their computers.
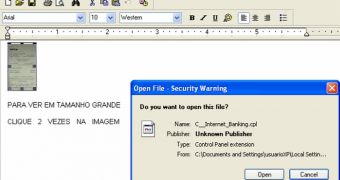
According to Kaspersky experts, the attack starts with an email that carries an RTF document named Comprovante_Internet_Banking.rtf (Receipt from Internet Banking). When opened, the document shows an image thumbnail and a message which instructs users to double-click on it to view it in larger size.
When the thumbnail is clicked, the victim is presented with a security warning that a CPL file is about to be executed. If the warning is ignored, the infection process begins.
The piece of malware that’s distributed in this campaign is part of the Trojan.Win32.ChePro family, a banking Trojan that’s popular among Brazilian cybercrooks.
So how did the attackers attach the malware to the innocent-looking document? They leveraged the fact that the RTF file format and text editors allow for objects, even executables, to be placed inside documents.
More technical details on this attack are available on Kaspersky’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //