Security researchers from Comodo have identified a new version of the notorious banking Trojan known as ZeuS. The variant analyzed by experts is signed with a valid digital certificate, which makes the threat more difficult to detect and remove.
More than 200 of Comodo’s customers have been targeted with this threat. Cybercriminals are distributing the malware with the aid of spam emails, or via exploits planted on malicious or compromised websites.
In the first phase of the attack, the downloader is distributed. Once this component finds itself on a device, it downloads a rootkit, which ensures the threat’s persistence, and the malware component.
The malware component is typical for ZeuS. It launches man-in-the-middle attacks to steal sensitive information, particularly financial data. The rootkit is designed to hide the malware and make it more difficult to remove.
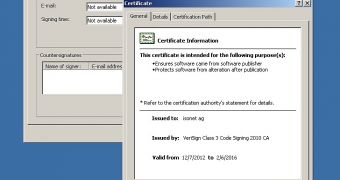
When it’s pushed onto a device, the Trojan looks like an innocent Internet Explorer file. This file is signed with a digital certificate apparently stolen from Swiss software company isonet.
The rootkit components are downloaded from two different domains. The rootkit is installed within Boot Bus Extender to ensure that it’s loaded before other drivers when the computer boots up.
Additional technical details on this new ZeuS variant are available on Comodo’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //