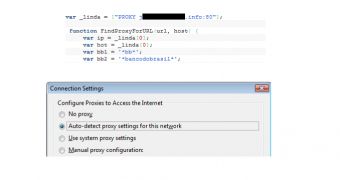
Cybercriminals are using malicious proxy auto-config (PAC) scripts in order to redirect webmail and online banking traffic through proxy servers they control. This tactic can enable them to seamlessly steal sensitive information such as usernames and passwords and even hijack authenticated sessions.
According to experts from Netcraft, the remotely hosted PAC scripts instruct web browsers to proxy certain requests. The attackers don’t target all requests in order to make the detection of their scheme more difficult and to limit the amount of traffic they must process.
The attacker could trick victims into using his proxy with the Web Proxy Autodiscovery Protocol (WPAD). Not all organizations utilize this feature, but some of them do.
In other situations, the attacker can social engineer the victim into changing his/her proxy settings. Moreover, the settings can be manipulated with the use of a piece of malware.
Up until recently, cybercriminals have used this technique only to target the customers of Brazilian financial institutions, but now they’re leveraging it to proxy traffic for popular webmail services and even PayPal.
 14 DAY TRIAL //
14 DAY TRIAL //