Security researchers from Malwarebytes have come across an interesting attack in which cybercriminals use social engineering, drive-by downloads, and extortion to achieve their malicious goals.
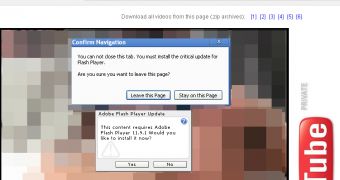
It all starts with a fake YouTube website that claims to offer adult videos. Users who visit the site are told to download a Flash Player update to view the content.
The so-called update file is an executable that bears a legitimate Flash icon, but in reality it’s a Trojan (Trojan.FakeFlash) which disables the Task Manager and creates registry entries to make sure it’s loaded every time the computer is started.
In addition to the bogus Flash Player update, victims are also given the possibility to download all the adult videos from the page.
The so-called videos are actually .scr (screensaver) files that hide a piece of ransomware detected by Malwarebytes as Trojan.Ransom.PARPE.
If internauts try to close the bogus YouTube page, they’re prevented from doing so by a simple JavaScript which keeps the window open even if the user presses the “Leave Page” button.
We’ve seen this technique being used by the OS X browser ransomware analyzed by Malwarebytes researchers a few weeks ago. According to experts, cybercriminals have started using this trick more often.
In the meantime, while the victim is busy trying to close the window, an exploit hosted on the page is used to infect the device with more malware.
These multi-pronged attacks are rarely seen in the wild, especially since stealthier attacks are more efficient.
“I wonder if the crooks behind this attack were just too greedy or perhaps wanted to test how good the ‘conversion rates’ would be,” Malwarebytes’ Jerome Segura wrote in a blog post.
Check out the technical details of this attack on the Malwarebytes blog.
 14 DAY TRIAL //
14 DAY TRIAL //