Over 190 clients of a large European bank have been targeted in a man-in-the-browser (MITB) campaign that allowed cybercriminals to pull at least half a million euros (approx. $680.000) out of their accounts.
MITB are attacks similar to man-in-the-middle campaigns, but differ in that the Trojan dynamically intercepts and manipulates calls between the web browser and its security mechanisms. Detecting this type of attack is quite difficult because all security controls are still displayed and work normally.
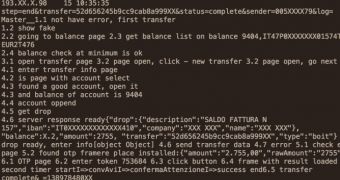
Researchers at Kasperky found evidence of the attack when they encountered a command and control server back in January this year. However, the crooks successfully deleted all the information that could lead to tracing them on January 22, two days after the discovery of the server.
In the two days they had at their disposal, the researchers analyzed the logs available and determined that more than 190 customers of a large bank in Europe, whose name remains undisclosed, had fallen victim to the heist.
The victims are from Italy and Turkey and had their accounts robbed of sums between €1,700/$2.300 and €39,000/$53,000.
The security experts could not determine the specific malware used in the campaign and speculate that it may be a Zeus variant that relies on sophisticated web injects.
“On the C&C server we detected there was no information as to which specific malware program was used in this campaign. However, many existing Zeus variations (Citadel, SpyEye, IceIX, etc.) – have that necessary capability,” said Vicente Diaz, Principal Security Researcher at Kaspersky Lab.
Nevertheless, they were able to determine that the malware exfiltrated usernames, passwords and OTP (one-time password) codes in real time.
The report from Kaspersky says that the money extracted from the victims’ accounts were distributed to three money-mule groups, each trusted with a limited sum of money to cash out from ATMs.
One of the groups was entrusted with large sums (up to €50,000/$68,000), another with medium values limited to €20,000/$27,000, while a third dealt with sums no larger than €2,000/$2,700.
This way, the masterminds of the operation ensured minimum losses because the members of this type of schemes oftentimes resort to cheating their partners.
Kaspersky named the campaign Luuuk after the path used by the administration panel on the command and control server: “/server/adm/luuuk/.”
It is possible that the campaign had been active for more than one week, in which case, the amount stolen is much higher. However, the researchers linked the campaign to professional criminals and future attacks are very likely to occur.
 14 DAY TRIAL //
14 DAY TRIAL //