A recent malicious campaign that lured users into clicking on a link to news about easy making of large amounts of money from home would use multiple redirects, some of the pages delivering the Nuclear Pack exploit kit.
It seems that the crooks are becoming more sophisticated in their attacks, making the scam as profitable as possible, as potential victims did not have to actually infect their computers to fill the scammers’ pockets; simply sharing one of the URLs provided by the crooks would be sufficient.
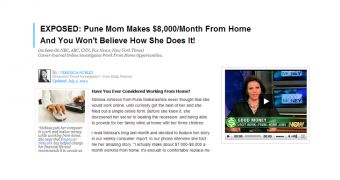
Security researchers from Symantec say that the lure is an article purporting to reveal how a woman makes $8,000 / €5,900 per month without having to leave her home.
Users interested in finding out more details click on the link and end up on another page that runs redirects to different online malicious locations.
In some cases, these deliver the Nuclear Pack exploit kit, known to leverage vulnerabilities in older versions of Java, Adobe Acrobat, and Adobe Reader.
However, in this example, the researchers say that the exploits used take advantage of security glitches in Microsoft Internet Explorer (CVE-2013-2551) and Java (CVE-2012-1723).
“After successfully exploiting a vulnerability, the Nuclear exploit kit drops Trojan.Ascesso.A. Trojan.Ascesso.A is known for sending spam emails and downloading other files from a remote location,” says Symantec’s Ankit Singh.
Telemetry from the systems of the security firm shows that the most affected regions are North America and Europe.
By enticing the potential victim to first share the malicious link, the crooks make sure that the scam perpetuates to other users.
A similar strategy that relies on multiple redirects to pages specially created to ensure the scammers make money in one way or another has been seen in the recent Facebook malicious campaign that purported to show the shooting down of the MH17 Malaysian airliner.
Users were blasted with all sorts of malicious actions, from being pushed software downloads, very likely as part of an affiliate marketing scheme, to being prompted to install fake updates for Adobe Flash in order to be able to watch the alleged footage.
By attempting different scams while the user accesses a single link, the success of the scam increases, especially since efforts are made to keep the user on the page that fires the redirects.
Users are warned to refrain from accessing links that appear suspicious, even if they are sent from a familiar individual, because they might have inadvertently participated in distributing the lure.
 14 DAY TRIAL //
14 DAY TRIAL //