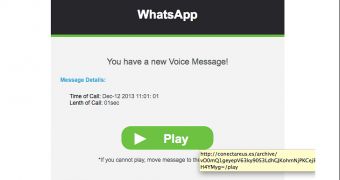
The WhatsApp “voice message” spam campaign that’s designed to distribute a piece of malware has been around for quite some time. However, experts from the Internet Storm Center (ISC) have recently made an interesting discovery in more recent variants.
When users click on the “Play” button in order to hear the so-called voice mail, they’re served a .zip file. What’s interesting about this file is the fact that its name depends on the victim’s location.
For instance, if you download it from Jacksonville, the file is named something like “VoiceMail_ Jacksonville_ (904)4581234.exe.”
It’s not only the name of the city that changes – the number in the file’s name is actually a phone number that matches the location of the victim’s IP address.
ESET products identify the threat as a variant of Win32/Kryptik.BQYU.
In case you come across such emails, act with caution. Unless you’re certain that it’s a legitimate notification (the links must point to a genuine WhatsApp domain), delete it at once.
 14 DAY TRIAL //
14 DAY TRIAL //