In August 2013, Symantec revealed the existence of a cybercriminal operation targeting European organizations, particularly ones in France. Over the past months, the attackers behind the campaign, dubbed Operation Francophoned, have made some changes.
Operation Francophoned attacks rely on a combination of social engineering and spear phishing emails. First, the attackers send a spear phishing email apparently containing an invoice to an employee of the targeted multinational company.
Then, they call the recipient and tell him/her to process the invoice. The so-called invoice is actually a piece of malware that gives the attackers access to the organization’s systems.
In October, researchers noticed a new attack. Between October 2013 and January 2014, the cybercriminals used the same type of social engineering techniques and the same piece of malware, Shadesrat or Blackshade.
However, they used new compromised domains to host the malware. Furthermore, they also became more aggressive when calling the victims to trick them into opening the malicious email.
In February 2014, experts spotted some significant changes. The cybercriminals replaced the payload with a new version of Trojan.Rokamal. They also started utilizing new compromised domains to serve the payload.
While they kept the old command and control (C&C) servers, the fact that they started using a new piece of malware resulted in an increase in the number of infections.
Rokamal is capable of performing various tasks, including downloading and executing other threats, launching DDOS attacks against designated targets, stealing information, mining crypto currencies and opening a backdoor to the infected computer. However, experts note that the DDOS and mining features have been disabled, most likely because they would make the malware easier to spot.
Government (24%), education (24%), research (14%), manufacturing, energy and automotive (7%) are the sectors most targeted by the group.
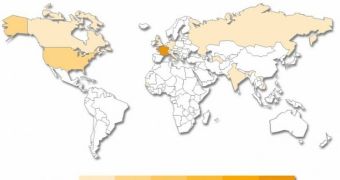
Symantec highlights the fact that despite an attempt to step up their game, the cybercriminals still mainly focus on organizations in France, or ones with French speakers outside of the country.
“Operation Francophoned was specifically crafted to target French speakers and proves that language is a major (and often underestimated) factor in the reach and effectiveness of cybercrime campaigns,” Symantec noted in its report.
Just because it focuses on French speakers, it doesn’t mean Francophoned is a small campaign. The attackers have plenty of victims to choose from. French is the official language in 29 countries. A total of 300 million people use it as their first or second language.
 14 DAY TRIAL //
14 DAY TRIAL //