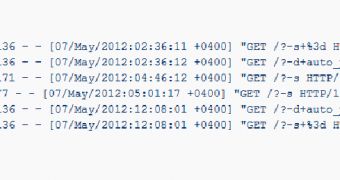
Security researchers from Trustwave’s SpiderLabs have noticed that one of their honeypots has recorded a number of attempts to exploit the recently uncovered PHP-CGI vulnerability.
For now, no successful exploits have been identified, but it’s clear that cybercriminals are probing systems in search for the vulnerability, in some situations even trying to execute remote code.
Experts recommend the use of security filters in the interim. SpiderLabs developed a ModSecurity rule that checks for four of the most common PHP command line arguments placed after the “?” symbol in order to start the query_string.
The rule, which applies an URL decode and removes whitespaces, looks like this:
SecRule QUERY_STRING "\?-[sdcr]" "phase:1,t:none, t:urlDecodeUni,t:removeWhitespace, block,log,msg: 'Potential PHP-CGI Exploit Attempt'"
The researchers also warn that some of the workarounds issued previously may not be as effective, because they would not catch some of the Request For Information (RFI) attempts to execute remote PHP code.
 14 DAY TRIAL //
14 DAY TRIAL //