The notorious piece of malware known as Sality has been around since at least 2003. However, over the past months, its developers have started adding new functionality, namely a component that’s designed to hijack the primary DNS address of routers.
Security researchers from ESET have been analyzing this new component, which was first seen at the end of October 2013. The threat, dubbed Win32/RBrute, was first spotted by experts from Russian security company Dr. Web.
In the first part of an attack, a component detected by ESET as Win32/RBrute.A scans the Web for various router models. The list includes D-Link, Cisco, Huawei, ZTE and TP-Link routers. Most targeted models are from TP-Link.
When one of these routers is identified, the malware downloads a list of IP addresses from the command and control server, and tries to perform a brute-force attack on the device’s administration panel.
The C&C server sends the bot a list of around a couple of dozen common or default passwords to try and access the administration page. The list includes “password,” “qwerty,” “root,” “trustno1,” “admin,” “12345,” “123456,” “abc123” and “administrator.”
Once access is obtained, the router’s primary DNS server address is changed. By changing the server’s address, cybercriminals can redirect users to arbitrary web pages.
ESET experts have found that users whose computers are infected will be redirected to a fake Google Chrome installation site whenever domains containing the words “google” or “facebook” are requested.
The fake Chrome pages are set up to distribute Sality. This way, other users that might be relying on the infected router can get infected.
“The IP address used as the primary DNS on a compromised router is part of the Win32/Sality network. In fact, another malware, detected by ESET as Win32/RBrute.B, is installed by Win32/Sality on compromised computers and can act either as a DNS or a HTTP proxy server to deliver the fake Google Chrome installer,” ESET’s Benjamin Vanheuverzwijn explained.
Based on their analysis, researchers have determined that the same group of developers is behind both the main file infector and the new components.
Experts say that this operation is similar to the one that relied on the notorious DNSChanger, which infected millions of computers worldwide and redirected their owners to arbitrary domains.
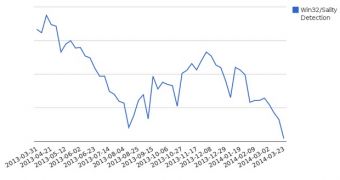
The number of Sality infections has steadily decreased since 2012. However, around December 2013, a small increase was recorded. This increase coincided with the malware being released in the wild.
For additional technical details on this new Sality component, check out ESET’s We Live Security blog.
 14 DAY TRIAL //
14 DAY TRIAL //