Experts warn that cybercriminals are relying on vishing (voice phishing) attacks to trick the customers of United States financial institutions into handing over their personal and financial information.
When people think about phishing attacks, they usually think about the fake login pages designed to replicate the ones of popular services. However, phishing can take other forms as well and vishing is a perfect example.
The principle is the same, but in visihing attacks, the cybercriminals send potential victims SMS messages instructing them to call a certain number and provide information.
PhishLabs has observed several such attacks against the customers of US banks. Last week, the company spotted a campaign aimed at the customers of a midsize bank.
Targeted individuals received text messages informing them that their debit cards had been deactivated. In order to “reactivate” them, victims are instructed to provide their card numbers and PINs.
The data stolen in such attacks can be used to perform fraudulent transactions or it can be encoded onto blank cards which can be utilized to withdraw cash at ATMs.
Many card issuers use track 2 data – CVV1 (Card Validation Value) or CVC1 (Card Validation Code) – to authenticate transactions. Since track 2 data is not printed on the physical card, fraudsters can’t obtain the data from cardholders. This means that they can’t clone cards, so they can only abuse the harvested data for fraudulent transactions.
On the other hand, some card issuers and payment processors don’t authenticate the CVV1 and CVC1 codes, allowing criminals to clone cards and directly withdraw funds.
Based on the analysis of a cache of stolen data, experts estimate that a single group has managed to harvest the details for around 250 cards per day. One of the phone numbers associated with the malicious campaign has been utilized in such attacks since October 2013.
The group whose activities have been monitored by PhishLabs appears to be based somewhere in Eastern Europe.
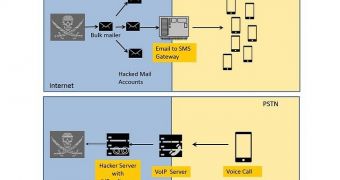
The cybercriminals rely on various systems to carry out their operations. First, they set up a server on which they install IVR (Interactive Voice Response) software. These are usually vulnerable servers that the attackers can easily compromise.
Then, they hijack the Direct Inward Dialing (DID) function on vulnerable VoIP servers, and assign a hacked phone number to the IVR system. They create a recording of the message that victims hear when they call.
The recordings, which are usually created with text-to-speech software, are loaded into the IVR system.
Once everything is set up, they send out SMSs to potential victims by using email-to-SMS gateways. The messages contain the phone number that users must call to “reactivate their cards.”
The VoIP server redirects calls to the IVR system where victims are asked to provide the financial information. The information is stored locally or on a remote server from which the cybercriminals retrieve it later.
 14 DAY TRIAL //
14 DAY TRIAL //