A custom-made malware, dubbed Dexter, has been found to infect hundreds of point of sale (POS) systems in an attempt to steal credit card details.
While some cybercriminals try to harvest payment card and other financial details by infecting the computers of millions of users with pieces of malware such as ZeuS, others try to obtain the same type of information from other sources.
According to experts from security firm Seculert, Dexter – whose name stems from a string found in one of the malware-related files – has been successfully used over the past 2-3 months to infect the POS systems of hotels, retailers, restaurants and private parking companies.
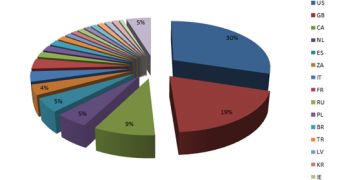
The threat has been targeting POS systems from 40 different countries. Most of the infections have been recorded in the United States (30%), the United Kingdom (19%) and Canada (9%).
Other countries such as the Netherlands, Spain, South Africa, Italy, France, Russia, Poland, Brazil, Turkey, Latvia and Korea are also on the list.
“Dexter is stealing the process list from the infected machine, while parsing memory dumps of specific POS software related processes, looking for Track 1 / Track 2 credit card data. This data will most likely be used by cybercriminals to clone credit cards that were used in the targeted POS system,” Seculert experts explained.
For the time being, it’s uncertain how the POS systems have been infected, but experts highlight the fact that more than 30% of the targeted devices are running Windows Server operating systems.
30% is an unusual percentage for infection methods that rely on web-based social engineering or drive-by downloads.
Other targeted systems have been found to be running Windows XP (51%), Windows 7 (7%), Windows Vista and Windows 2000.
 14 DAY TRIAL //
14 DAY TRIAL //