The latest version of CryptoWall has been spotted to be delivered with a piece of spyware that ensures the cybercriminals still get an opportunity to make money if the victim has a proper backup system in place.
The infostealer added to the infection routine is Fareit, known for its ability to trawl credentials from programs ranging from email clients, web browsers, FTP clients and digital currency wallets.
Malware payloads are disguised as JPGs
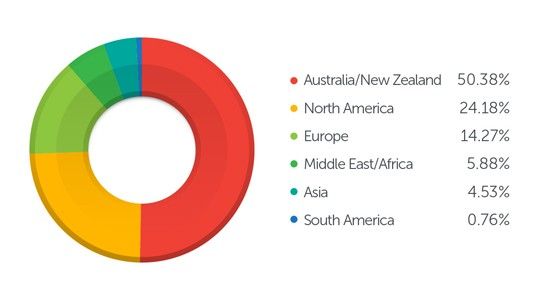
Telemetry info from security company Trend Micro shows that users in Australia and New Zealand are most affected by the nefarious tandem, accounting for about half of the recorded infections.
They are followed by North American users, where the CryptoWall and Fareit pair has been detected in 24.18% of the cases, and those in Europe, with 14.27% infections. Other regions impacted are the Middle East/Africa, Asia and South America.
Security researchers at Trend Micro say that the dropper for the two pieces of malware comes as an archived JavaScript (JS) attached to an email claiming to deliver a resume.
The choice of using a JS file can be explained by the fact that some scanners do not check this type of data.
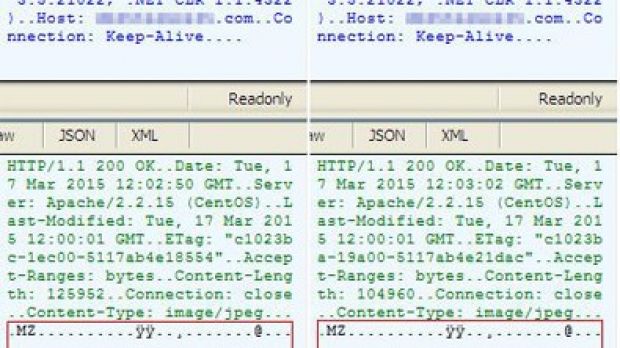
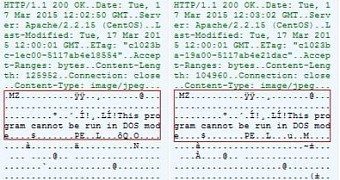
The analysis of this file revealed that it connects to two command and control (C&C) servers to download two apparent image files in JPG format. However, this is only a ploy to bypass intrusion detection systems (IDS).
Looking deeper into the JavaScript showed that the two files are actually executables for CryptoWall and Fareit, which are run immediately after being downloaded.
Increasing the chances for profit
Anthony Joe Melgarejo, threat response engineer at Trend Micro, says that while CryptoWall encrypts the targeted file types (documents, databases, emails, images, audio, video, and source codes) in the background, Fareit runs its sensitive info snatching routine and sends the data to the C&C.
The ransomware locks the items with a strong RSA-2048 key and changes their extension to a random one. In the affected folders, it also drops instructions on how to make the ransom payment (about $500 / €460), which is in bitcoin currency and it is carried out via a payment website in TOR anonymity network.
Coupling ransomware with an infostealer is a relatively new technique that has been seen in the past with VaultCrypt crypto-malware, which relies on open source GnuPG to lock down the files.
This is seen as a fallback plan for cybercriminals to obtain some profit even if the victim has the option not to pay the ransom fee because of existing data backups or they simply refuse to do so in order to discourage this nefarious practice.
 14 DAY TRIAL //
14 DAY TRIAL //