Relying on multiple infection vectors, Cryptowall managed to achieve wider presence than the infamous CryptoLocker, affecting 625,000 systems across the world in a period of about five and a half months.
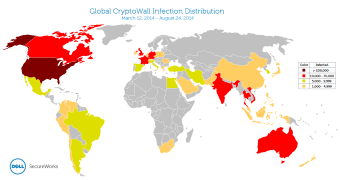
Recorded by Dell SecureWorks Counter Threat Unit (CTU), most of these infections were traced in the United States because of the numerous malicious campaigns targeting English-speaking users.
The security researchers say that the total number of files encrypted by CryptoWall in the monitored timeframe (mid-March until August 24, 2014) amounted to 5.25 billion files.
CryptoWall has been seen being distributed through various methods, from drive-by downloads to exploit kits and spam campaigns.
By sinkholing one domain used as a backup command and control server by the attackers, CTU could observe that 40.6% of the infected machines were located in the US, accounting for 253,521 of the total number.
Far on the second place was Vietnam, with 66,590 machines infected (10.7%), followed by the United Kingdom, recording 6.4% of the infections (40,258). Other countries affected include Canada (32,579), India (22,582), Australia, (19,562), France (13,005), Germany (12,826) and Turkey (9,488).
The threat actors behind CryptoWall are organized and use identification codes for each sample, representing the malicious campaign that distributed them.
According to the researchers, five campaigns distributing the ransomware are currently in use, relying on the spam spewing the Cutwail botnet, Gozi/Neverquest and Magnitude exploit kit.
At the beginning, CryptoWall would pretend to be CryptoLocker, but its simpler architecture did not fool security researchers who quickly noticed that it was a different threat.
However, after CryptoLocker was taken down back in June this year, CryptoWall took its place as the most prevalent crypto-malware and even managed to cause more infections across the globe.
Despite compromising 100,000 computers more than CryptoLocker, CryptoWall caused smaller financial damage, collecting only “37% of the total ransoms collected by CryptoLocker.”
Contributing to its smaller success may be the fact that the operators behind it do not have highly organized “cash-out” and laundering services as those handling CryptoLocker.
“In mid-March 2014, CryptoWall emerged as the leading file-encrypting ransomware threat. The threat actors behind this malware have several years of successful cybercrime experience and have demonstrated a diversity of distribution methods. As a result, CTU researchers expect this threat will continue to grow,” says the report from Dell SecureWorks.
The ransomware starts locking the data on the compromised computer after retrieving the RSA public key from the command and control (C&C) server; blocking communication to this location results in failure of the encryption process.
The researchers reported that from the 625,000 infections recorded over the monitored period, only 1,683 victims paid the ransom, increasing the profits of the cybercriminals by more than $1.1 million / €835,000.
The lowest ransom was $200 / €152 and it was paid six times. However, most of the victims paid the $500 / €380 ransom, and the security researchers also saw that one person made a $10,000 / €7,580 payment to the crooks.
 14 DAY TRIAL //
14 DAY TRIAL //