The new version of the CryptoWall ransomware was first noticed at the beginning of October, and since then, no less than 84 variations have been detected by security researchers.
Recently, this piece of malware with file encryption capabilities has been used in a massive malvertising campaign on prominent websites such as Yahoo, AOL, 9Gag and major news publications in Australia.
TOR communication enabled, 85,000 attacks recorded for CryptoWall 2.0
In a blog post on Wednesday, Ryan Olson from Palo Alto Networks says that, although starting September 30 telemetry from their systems showed increased activity for CryptoWall 2.0, more and more variants are popping up on a daily basis.
F-Secure was the first to observe the official 2.0 version of the malware, which included capabilities that had been tested in version 1.0.
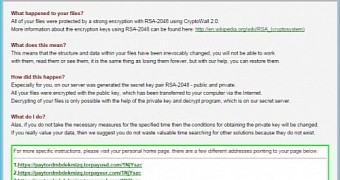
One of the modifications includes communication with the command and control (C&C) server over TOR (The Onion Router) anonymization network, which is now built into the crypto-malware. This allows the attackers to hide the C&C servers and avoid them being taken down by law enforcement. On the same note, only Bitcoin digital currency is accepted as ransom.
Olson says that since CryptoWall 2.0 was first detected by Palo Alto Networks, more than 85,000 attacks have been recorded to try to deliver the malware.
“The majority of these have come through e-mails with executable attachments, sometimes contained in .zip files,” he says.
CryptoWall expands rapidly, victimizes hundreds of thousands
This crypto-malware in particular appears to have been adopted at a large scale, as it has been seen to be delivered through multiple exploit kits (EK).
French vulnerability researcher Kafeine saw it in Nuclear Pack EK, while in the recent malvertising campaign, it was funneled in by FlashPack EK.
In August, Dell SecureWorks published a report saying that over 625,000 victims had been recorded in a period of five and a half months, with an estimated $1.1 million / €835,000 being collected by the cybercriminals.
In a different malvertising campaign in September, a version of CryptoWall signed with a digital certificate from Comodo was seen to be delivered to victims.
One of the latest attacks observed by Palo Alto Networks had the malware connect to four domains registered on Wednesday, all resorting to a Russian IP address associated with an email that has been used with other two payment domains registered earlier this month.
“If these domains are confiscated or otherwise shut down, CryptoWall instructs the user to download the Tor Browser and access a website (paytordmbdekmizq.onion) that is only accessible over the Tor network,” said Ryan Olson.
Bottom line is that the number of attacks involving CryptoWall has increased lately and the trend does not appear to slow down, especially with the shopping season coming up, when people are more likely to land on dodgy websites in search of bargains.
 14 DAY TRIAL //
14 DAY TRIAL //