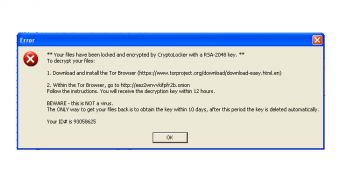
A modification of the infamous CryptoLocker ransomware Trojan that does not rely on the 2048-bit RSA encryption and does not communicate with a command and control server has been found in the wild.
Although the GameOver Zeus botnet, also used by cybercriminals to distribute CryptoLocker ransomware, has been dealt a heavy blow by law enforcement agencies, variants of the file-encrypting malware are still available in the wild.
A post from Fakebit shows an analysis of a CryptoLocker spin-off that instructs the victim to access a location in the TOR network to receive details about the ransom payment.
The Trojan appears to encrypt data on the affected computer, but it does not rely on an asymmetric cryptosystem to carry out the job as the ransom message says. Instead, it seems to use a symmetric cipher that is weaker and can be broken in order to regain access to the locked files.
“The constant 0x9e3779b9 seems to be important, appearing at several points of the encryption function. An internet search for this constant shows that it is a magic number commonly used in the Tiny Encryption Algorithm (TEA),” says the researcher.
However, the malware still presents the danger of data encryption. The items affected from executables and multimedia files (image, audio and video) to documents and ebooks; their extension is switched to CRYPTOLOCKER.
According to the analysis, there is “some indication that this malware is capable of decrypting the files on the filesystem. There are strings that appear to be prompts and responses for decryption password input.”
After patching the binary to instruct the execution of the decryption function and then removing the CRYPTOLOCKER extension, the researcher managed to unlock the data, proving that the Trojan does not use an asymmetric cipher.
Judging by the simplicity of the encryption algorithm and the chosen method for receiving payment, this CryptoLocker variant can be considered a weak imitation of the original; but even so, by relying on the limited knowledge of the victim, cybercriminals could rake in some serious cash.
In this case, the Tor location with the instructions for paying the ransom no longer works, which could leave affected users that do not have the necessary tool to reverse the encryption process without their files.
Similar types of ransomware can appear at any time from less experienced crooks trying to make a quick buck. Security researchers recommend against paying the money in order to discourage ransom practices and because there is no certainty that cybercriminals keep their end of the deal and provide the decryption.
 14 DAY TRIAL //
14 DAY TRIAL //