Users whose files have been encrypted by the infamous CryptoLocker now have a chance to recover their data without having to pay the ransom fee demanded by the cybercriminals.
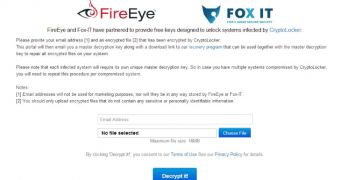
The service is provided by FireEye and Fox IT and is available as a web page where users can submit an encrypted file sample for analysis.
As soon as the assessment is complete, the user is sent an email with the master private key required for decrypting the data.
Since many users may not know what to do with the decryption key, the service also provides a download link for a tool, called Decryptolocker, that can be used to facilitate the unlocking of the data.
Although CryptoLocker has been dismantled by Operation Tovar, which joined multiple law enforcement agencies and private security organizations, several variants of the malware have been created, with slight differences in functionality; keep in mind that this decryption service may not be successful with all of them.
The service is free of charge, but a valid email address is required for the delivery of the tool designed to decrypt the data. Both companies inform that the emails will not be used for marketing purposes, nor will they be stored on their systems.
It is recommended to upload a file that does not contain any sensitive information, in order to make sure that privacy is not affected in any way by the service.
CrytpLocker encrypts the data on the entire system with a single key; as such, only one decryption key is necessary to have access to the files on a computer. However, the same key cannot be used on multiple systems and samples from each of them have to be uploaded for receiving the corresponding keys.
Working with Decryptolocker is not difficult, but it requires launching the utility from Windows Command Prompt, an environment most users are not accustomed to.
There are multiple ways for a computer to get infected with CrytoLocker, but the most prevalent attack vector is phishing; watering hole attacks have also been observed to deliver this malware.
As soon as the computer is compromised, the malicious software connects to a command and control server to download the master public key used for encrypting the data.
Security researchers recommend not to pay the ransom requested by the cybercriminals because they may not keep their end of the deal and fail to deliver the decryption key.
Creating file backups stored in a different location ensures that if CrytptoLocker hits, no important information is lost and can be recovered from the safe copy.
 14 DAY TRIAL //
14 DAY TRIAL //