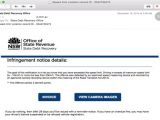
A new ransomware trying to monetize on the name of the infamous CrytoLocker ransomware has been observed to be served to unsuspecting Australians in emails claiming to be from the Office of State Revenue, in connection to paying a fine for speeding.
Although the malware claims to be CryptoLocker, security researcher analyzing a sample determined that it had no relation with the original and it was only a copycat.
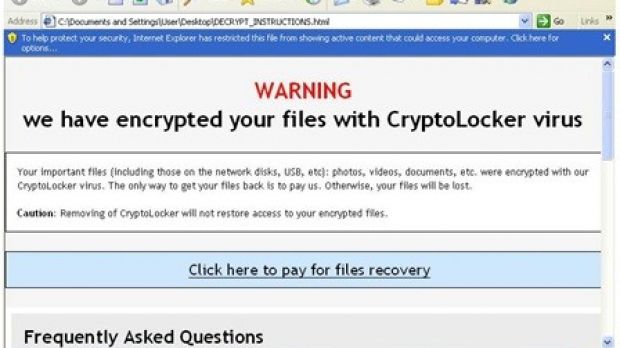
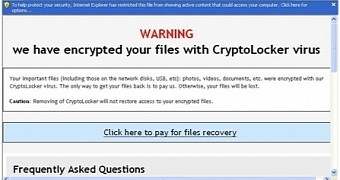
However, this does not eliminate any risk because the malware does have encryption capabilities and locks files once it is launched on a computer. As soon as this process is over, a ransom message pops up informing of the locked state of the data and asking for a fee to unlock it.
Security experts at Barracuda Labs, who caught the sample, say that on Wednesday the detection rate of the malware was very low on Virus Total, only one antivirus engine in 54 labeling the file as a threat.
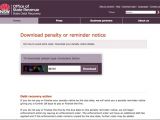
In a blog post on Thursday, they showed a sample of the email delivered by the attackers, which contained two links, one claiming to lead to the invoice, the other to speeding image proof caught on camera; however, both direct the potential victim to a location hosting the crypto-malware.
Both the initial email and the website hosting the malware are created to look legitimate and have the potential of tricking a lot of Australians into launching the ransomware on their systems, in an attempt to check the alleged proof of speeding.
To give credibility to the email, the malicious actors placed a real captcha gate for downloading the ransomware disguised as legitimate files.
Protection against crypto-malware can be achieved by creating regular backup copies of the sensitive data; this would allow restoration of the originals in case of an infection.
 14 DAY TRIAL //
14 DAY TRIAL //