Last month, researchers from ESET discovered what appeared to be a new variant of the notorious CryptoLocker ransomware. The threat is dubbed CryptoLocker 2.0, but experts believe that it’s not developed by the same individuals who created the older version.
CryproLocker 2.0 is similar to CryproLocker. It scans infected computers for certain file types and encrypts them using RSA public-key cryptography. It then demands the payment of a certain amount of money to have the files restored.
However, a closer analysis reveals that there are a lot of differences between the two. Furthermore, there are no significant improvements in the new variant of the malware.
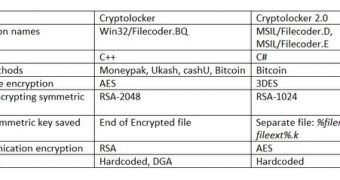
For instance, CryptoLocker is written in C++, while CryptoLocker 2.0 in C#. The 2.0 version is designed to accept payment only in Bitcoin, unlike the older one that also accepts Ukash, MoneyPak and cashU.
As far as the encryption is concerned, CryptoLocker 2.0 claims to use an RSA 4096-bit cipher, but it actually utilizes RSA 1024-bit, which is weaker than the original version that uses RSA 2048-bit.
When it comes to command and control (C&C) communications, the old variant of the ransomware uses an RSA public key for encryption, while CryptoLocker 2.0 relies on AES. Another noteworthy thing is the fact that CryptoLocker 2.0 uses hardcoded C&C addresses, while the original version contains a domain generation algorithm (DGA) as well.
Interestingly, CryptoLocker 2.0 is designed to mimic cracks and activators for various pieces of software, such as Microsoft Office, Windows, Photoshop and Team Viewer. Experts say that this serves as an additional spreading mechanism.
“The list of functionalities present in the trojan code is quite extensive and also includes stealing Bitcoin wallet files, launching the legitimate BFGMiner application or running DDoS attacks against a specified server. However, we were unable to establish whether this functionality was actually being used at present,” ESET’s Robert Lipovsky noted.
In conclusion, considering that there are a lot of differences between the two threats, CryptoLocker 2.0 is most likely the work of a copycat.
 14 DAY TRIAL //
14 DAY TRIAL //