Over the weekend, reports came in from users informing that their NAS (Network Access Storage) devices from Synology had become the target of cybercriminals, who created crypto-malware intended specifically for this type of storage.
Named Synolocker, the malicious file could land on the NAS devices either through brute-forcing the login credentials or by leveraging a vulnerability in DSM (DiskStation Manager) or in the operating system.
However, since Synology has not yet published a security advisory for their products, the former variant seems more plausible at the moment. Members of the Synology forum have contacted the company and received advice.
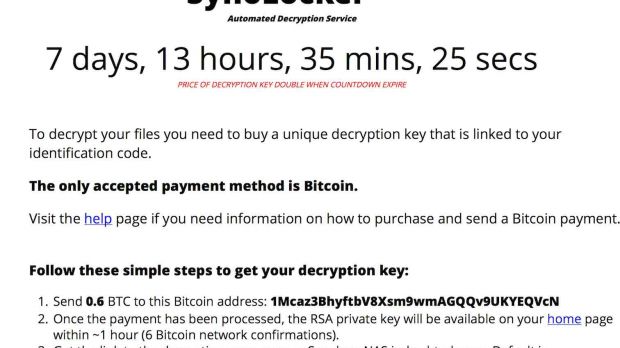
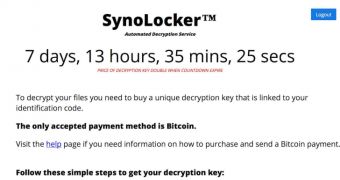
Synolocker is similar in action to the infamous CryptoLocker. After infecting the device, the Trojan starts encrypting the files on the disk, one by one, at the same time displaying a ransom message asking the victim to pay a 0.6 Bitcoin fee ($350 / €262) in exchange for the decryption key.
A TOR (The Onion Router) address is provided for completing the transaction, and after the money is transferred, the crook says that the file unlocking the RSA private key would be made available on the main page of the webserver. Complete instructions about what to do to recover the data are also provided.
Despite the above grim scenario, there are methods to prevent the crypto-malware from infecting the NAS device, as well as for saving at least some of the data, while the encryption process begins.
Users that have already been affected by Synolocker are advised to turn off the DiskStation as soon as they learn about the infection.
Since the malware encrypts files one by one, there is the possibility to stop the locking process and save some of them through migration to a different, clean storage device; this method is not foolproof, though, since determining when the encryption process, which runs in the background, began is critical and in many cases it may be too late.
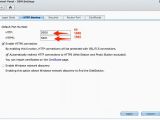
The solution for preventing Synolocker from infecting the NAS is quite simple, and consists of several steps. The router has to be configured to stop forwarding traffic to the router (where available), the default port needs to be changed, and a strong password needs to be instated. Updating to the latest DSM version is also on the list of recommendations.
As soon as these steps have been taken, it would be wise to make a backup copy of the data on the DiskStation, just to stay on the safe side. It is recommended to remove the remote access to the device.
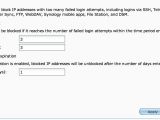
Another measure of protection is to activate the AutoBlock feature, which blocks connections from IP addresses with multiple failed login attempts.
 14 DAY TRIAL //
14 DAY TRIAL //