A new strain of crypto-malware is currently affecting Russian-speaking countries, with functions that allow it to steal email addresses and corresponding addresses, as well as to spread on its own to the victim’s email contacts.
Apart from these particularities of the malware, security researchers note that it is written in a batch file and used multiple freely available tools to carry out its dirty work.
The attack vector is a Word document delivered via email, which claims to include a change in the terms of agreement of a service that needs to be reviewed before signing.
As soon as the victim opens the document, a downloader written in JavaScript funnels in a bunch of executables masked with the BTC extension. These are free, publicly available tools necessary for encrypting the data stored on the computer as well as for propagating the malware.
Jaromir Horejsi and Honza Zika of Avast analyzed the threat and noticed that all the malicious actions were initiated by a BAT file.
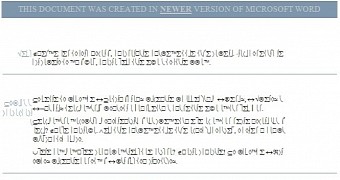
To mask the process of encrypting the files (XLS, XLSX, DOC, DOCX, XLSM, DWG, SVG, MDB, PDF, ZIP, RAR, and JPG being among them) on the disk, the Word document is displayed, only to show gibberish characters, the reason for this being motivated by the fact that it had been created with a newer version of Microsoft’s Word processor.
Behind the scenes the data is locked up with RSA 1024-bit algorithm, and relies on public-key cryptography that involves a public key encrypting the data, and a private one for decrypting it, which is sent to the attacker in this case.
A ransom message is displayed, asking the victim to pay €140 / $185 for the private key that unlocks the files, and send two files (UNIQUE.PRIVATE and KEY.PRIVATE.) to an email address ([email protected]) controlled by the cybercriminals.
These items are required for identifying the information that has been encrypted and its location on the disk, and for providing the decryption key.
In order to spread to as many victims as possible, this malware steals email credentials from the browser, pulls the sender information from the freshest 100 emails and delivers them a custom message, with the downloader hidden in an attachment.
The email usernames and passwords are also sent to the attacker and then tested on webmail services common in Russia: Mail.ru and Yandex.
Interesting about the propagation method is that the 100 messages downloaded from the victim’s inbox are filtered, and the ones received automatically are eliminated.
Furthermore, ten variants of emails are created, each with a custom link pointing to different files hiding the JavaScript downloader.
“The virus now has a fake email with a malicious link, addresses to send it to, and the email address and password of the sender. In other words, everything it needs to propagate. Propagation is achieved using program Blat renamed as spoolsv.btc,” write the researchers in a blog post.
This is not a typical ransomware, as it leverages free software like GPG (for encryption), Email Extractor, Browser Password Dump (for retrieving passcodes stored in the web browser) and Blat (for sending email).
After the nefarious activity is completed, all the temporary files are deleted from the system using the SDelete tool from Sysinternals, part of Microsoft.
 14 DAY TRIAL //
14 DAY TRIAL //