A ransomware with file encryption capabilities is currently flung at company workers responsible for screening resumes from job seekers.
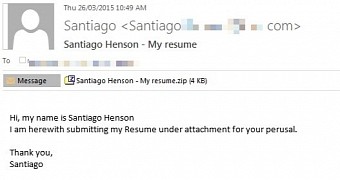
The malware piece is distributed via a short email message that informs about the availability of a curriculum vitae in the attachment, inviting the recipient to open it.
Message looks credible, harbors CryptoWall
It is unclear if the attacks are targeted or the cybercriminals sent off a batch of such messages hoping to catch some victims.
To eliminate suspicions of foul play, the crooks include a short introduction of the alleged job candidate by giving a name and pointing to the file in the attachment for more information.
“Hi, my name is [first and last names removed]. I am herewith submitting my Resume under attachment for your perusal. Thank you,” it is written in a sample of the malicious email.
The attached document, however, is an archive that contains a JavaScript code with instructions to download a variant of CryptoWall ransomware.
As soon as the malware is executed on the computer, it starts encrypting files on the hard disk, holding the data hostage until a fee is paid in exchange for the decryption key.
CareerBuilder services have also been exploited for malware delivery
Delivering malware via email is an old practice, but cybercriminals have started recently to employ new methods for infecting systems operated by users that handle resumes.
Security researchers at Proofpoint alerted at the beginning of the month that CareerBuilder employment website had been used for nefarious purposes aimed at the same type of victims.
The operation consisted in submitting a reply for a job listing, which was relayed to the job poster without being processed in any way. Thus, the crooks leveraged the reputation of CareerBuilder to deliver their malicious software, the victim being unaware that the message was received exactly as intended by the alleged job seeker.
The chances of compromise are high in this case because the recipient expects such an email and trusts the intermediary service that delivers it.
 14 DAY TRIAL //
14 DAY TRIAL //