The use of multiple crypto-malware families have been observed to increase significantly more in Australia since about the second half of the year, than in other parts of the world.
Threats like CryptoLocker, CryptoDefense and CryptoWall are a global problem, but users on the smallest continent on earth have to deal with them more often than anywhere on the globe.
According to telemetry from security firm Symantec, the use of ransomware with encryption capabilities recorded a roughly 14 times increment since May, but in Australia the surge was of more than 1,300%.
Fake email from local companies points to crypto-locker
The social engineering skills of cybercriminals are well known, and in Aussieland, they’re putting them to use in emails delivering a variant of the infamous CryptoLocker.
Crooks devise messages for specific geographic regions to ensure a greater rate of success. As such, emails claiming to be from local companies like energy suppliers or postal delivery organizations are commonly carrying the ransomware.
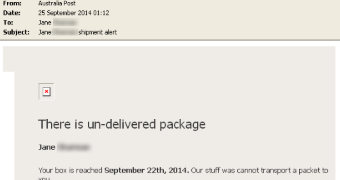
“In Australia, users are sent emails that typically look like they came from local companies such as an Australian energy supplier (view a bill) or an Australian postal delivery company (details of parcel delivery),” Symantec says.
Once the potential victim accesses the malicious link in the email, they are directed to a phishing page that looks very similar to what they expect to see; they are asked to enter a CAPTCHA code to view the message from the company.
CAPTCHA strings are generally used on legitimate websites to prove that a real human is accessing the service, not an automated system. This scenario applies in this case, as crooks try to make sure that security vendors cannot automatically download the sample in view of analysis.
After the code is entered, the potential victim is offered to download a ZIP archive, which contains the crypto-malware.
Users are advised to back up sensitive information
Ransomware with encryption capabilities lock up the files on the computer and demand a ransom to be paid. Unless weak encryption is used, which is not the case with CryptoLocker and the like, the chances to recover the data are slim.
Security researchers advise against paying up the money to retrieve the information in order to discourage such practices; instead, the money can be invested in a backup solution that allows restoring the files if crypto-malware grabs hold of the data.
Apart from this, once they receive the money, crooks have no incentive to deliver the decryption key and keep their word.
On the same note, Symantec recommends staying vigilant and highly suspicious of unsolicited emails purporting to be bills or other services.
 14 DAY TRIAL //
14 DAY TRIAL //