The root certificate used by Superfish browser add-on that came pre-installed on Lenovo laptops has been extracted and the password that encrypted it has been cracked.
Recently, it has been discovered that the Superfish software on consumer notebooks from Lenovo used a self-generated root certificate to re-sign all certificates from HTTPS websites, banks’ included, allowing it access to plain-text information in traffic that would otherwise be encrypted between the client and the server.
Researcher creates custom brute-force program
Multiple security experts who looked into the matter revealed that the add-on used the same RSA key (1024 bits) on all devices, meaning that if someone managed to crack it, they would be able to peak into the encrypted traffic exchanged between a Lenovo user and a secure service; and this is exactly what Robert Graham, CEO of Errata Security, did on Thursday.
The security expert allowed a machine to get compromised by Superfish and then dumped the data created by the process in the memory of the system.
After finding the encrypted private key for the root certificate used by Superfish, and the certificate itself, he tried to take a look only to find that the data was password protected.
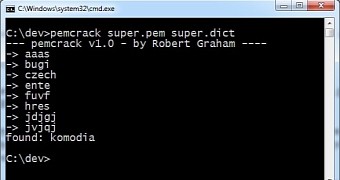
The task of cracking the password proved to be a bit more challenging than expected since it required writing a custom brute-force program. Graham relied on a dictionary attack to find the correct string and used the data in the memory dump in the process.
He assumed that the password would not be a complicated one, so he allowed only lower-case words to be tried by the brute-force solution he created; in no less than 10 seconds the string was discovered to be “komodia,” the name of the transparent-proxy used by Superfish to intercept communication.
Lenovo issues official statement
The password decrypts the root certificate that could be used in man-in-the-middle attacks against Lenovo users with Superfish installed on their system.
While security researchers debated on the risks posed by Superfish, Lenovo was not sitting idly and prepared an official statement, saying that the add-on was included on its laptops only between September and December 2014.
As a result of the large number of user complaints, the company decided to stop shipping products pre-installed with Superfish in January. Moreover, it contacted the software maker to disable all server-side interactions on all Lenovo systems, rendering the application inactive.
Lenovo also said that it would not preload Superfish in the future and that it would continue to review its actions that could have a negative impact on its customers.
 14 DAY TRIAL //
14 DAY TRIAL //