A blogger trying to bypass Twitter's new nofollow policy for oauth client application links stumbled upon a massive persistent cross-site scripting (XSS) vulnerability, which allowed him to insert potentially malicious JavaScript code into a tweet. The vulnerability could have been leveraged to steal session cookies, create a Twitter worm or infect visitors with malware.
Earlier this month, search engine optimization gurus revealed a black hat SEO technique that was being used to increase a website's page rank by receiving "link juice" from Twitter. Most of the links pointing out of Twitter have the rel="nofollow noopener" parameter, which tells search engine robots not to follow them.
However, one type of Twitter links that lacked this attribute were the ones pointing to the oauth client used to post a particular tweet, like Tweetdeck, Seesmic, Tweetie or others. These links appear underneath the actual message of each status update posted from outside of Twitter and reads something like: "[x] minutes ago from [Application Name] (linked)."
As it turns out, Twitter allows users to configure the name, description and URL for these third-party applications used to post tweets. SEO black hats figured out that the accuracy of this information is not verified in any way, meaning someone could have easily obtained a dofollow link for their own website, that gets repeated with each tweet.
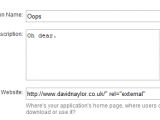
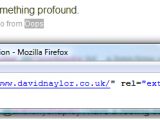
Twitter blocked this SEO hack by adding rel="nofollow noopener" to all oauth client application links. While attempting to bypass this fix, a blogger named James Slater noticed that the "Application Website" field in the form used to configure a Twitter client application allows for malformed input. He was surprised when http://www.example.com/" rel="external" was accepted as input and produced a valid rel="external" link overwriting the rel="nofollow noopener" parameter (see image below).
This gave him the idea to experiment with some more advanced code, only to realize that JavaScript can just as easily be inserted into the page through the same field. For demonstration purposes, Mr. Slater added code to prompt an alert in the visitor's browser when the rogue tweet is viewed. "Obviously if it could do that… the world is your oyster!" he writes.
More specifically, Slater points out that "If I was going to be mean, I could have made that JavaScript steal your login cookie and send it to us. Or maybe to someone else? Perhaps I could drop a few trending hashtags in there and see how many people look at my tweet. Or worse - why not use Twitter’s own handily-available API to, I dunno, post a few tweets?"
Twitter has been alerted about this vulnerability and John Adams of Twitter Operations confirmed yesterday evening that "We have patched this issue as of a few hours ago." Nevertheless, the level of security on Twitter is placed under the microscope again by the security community. Many professionals warned back in April after Mikeyy's worms were blocked, that it wasn't going to be the last time when critical cross-site scripting flaws would be discovered on the micro-blogging platform.

 14 DAY TRIAL //
14 DAY TRIAL //