A serious issue in the way the prevention system for cross-site request forgery works opened all PayPal accounts to hijacking, an independent researcher says.
The flaw is a cross-site request forgery (CSRF) and consists in the fact that PayPal has reusable authentication tokens that could be employed by an attacker to link their email address to the account of a victim and have access to options such as changing the password.
Re-usable authentication tokens
Moreover, Egyptian researcher Yasser Ali says in a blog post that he managed to capture an authentication token that was valid for all PayPal accounts.
In the first stage of the experiment, he discovered that the token responsible with authenticating any user request was not modified for an email address, allowing an attacker to carry out modifications, if authenticated.
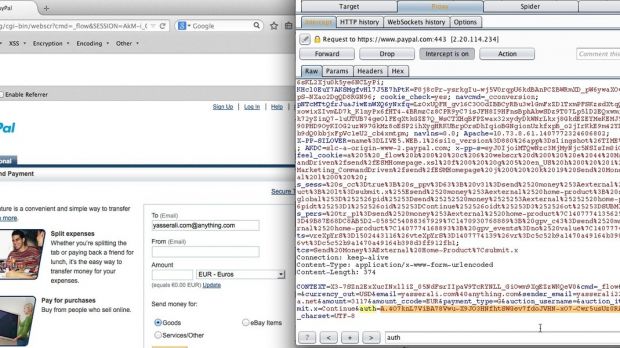
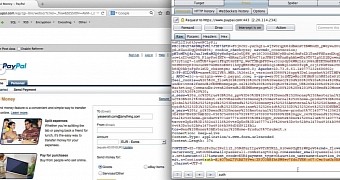
Carrying on the research, Ali observed that he could bypass PayPal's CSRF Protection Authorization System by intercepting an authentication token valid for all users. This was done using the Burp toolkit for getting the POST request from a page that includes a token before the log-in process.
The example provided by the researcher was a page for sending money to a different PayPal user. He entered the email of the sender and the recipient, as well as a bogus password, thus generating a token for the request for that specific account; Ali says that the token could be used for other requests too.
Modifying the account password
With this information discovered, Ali started to look for ways to change the password of a target account without being logged in, a process that could not be done without providing the correct answer to security questions. Reaching this stage would require the attacker to be logged in, though.
However, the request for defining the security questions occurs when signing up for the PayPal service, and it is not password-protected. As such, with the CSRF authentication token in hand, the attacker is free to change the questions and provide different answers.
Among the requests validated by the token there is adding, removing, and confirming an email address, changing the security questions, modifying the billing and/or shipping address, as well as changing the payment methods and account configuration.
Ali created a proof-of-concept video (available below) to demonstrate his findings and how they could be used in a real-life attack scenario.
All the flaws are fixed at the moment, as the researcher has made a responsible disclosure to PayPal through the Bug Bounty program. According to Ali, he received a $10,000 / €8,100 reward from the company.
[UPDATE, November 5]: A PayPal spokesperson contacted us about the vulnerability, reassuring that the fix was implemented before any customer was affected.
"One of our security researchers recently made us aware of a potential way to bypass PayPal's Cross-Site Request Forgery (CSRF) Protection Authorization System when logging onto PayPal.com. Through the PayPal Bug Bounty program, the researcher reported this to us first and our team worked quickly to fix this potential vulnerability before any of our customers were affected by this issue. We proactively work with security researchers to learn about and stay ahead of potential threats because the security of our customers’ accounts is our top concern," the email from PayPal reads.
 14 DAY TRIAL //
14 DAY TRIAL //