Security researchers have further analyzed Crisis, the new Mac OS malware that has been making a lot of headlines in the past few weeks. The most interesting thing they uncovered relates to the way this malicious element spreads.
It’s known that OSX.Crisis arrives on the computers of potential victims as a JAR file, but what happens once it lands?
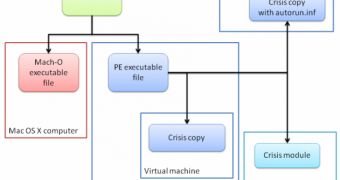
According to Symantec experts, the threat has the ability to spread not only to Mac and Windows computers, but also to virtual machines and devices that run Windows Mobile.
The .JAR contains malicious executable files for both Mac and Windows operating systems. The files are designed to open a backdoor on the affected device.
After checking to see which operating system is installed on the compromised computer – if Windows is detected – the malware searches for a VMWare virtual machine image. When it finds one, it mounts it using a VMware Player tool and copies itself onto the image.
“It does not use a vulnerability in the VMware software itself. It takes advantage of an attribute of all virtualization software: namely that the virtual machine is simply a file or series of files on the disk of the host machine,” Takashi Katsuki of Symantec explained.
“These files can usually be directly manipulated or mounted, even when the virtual machine is not running as is the case above.”
Unlike other threats that do their best to avoid ending up in a virtual machine, Crisis does the opposite.
The malicious element also has the ability to spread to removable disks as an autorun.inf file, but, more importantly, it has the capability to drop its modules onto Windows Mobile devices that are connected to the compromised computer.
Little is known about these modules, but the researchers claim that they don’t affect other types of phones because they use the Remote Application Programming Interface (RAPI) to copy themselves.
 14 DAY TRIAL //
14 DAY TRIAL //